The BMW CIC Mid is the Business Navigation system available in Europe, and never installed in vehicles intended for North America. As a resident of North America, investigation of the CIC Mid firmware is purely theoretical as I have no ability to verify the correctness of the reverse engineering, and therefore am not intending on releasing any keygen source code.
dump_hbcifs Source Code
Source code to dump QNX IFS, ImageFS, and HBCIFS is available on github here: https://github.com/ReverseEngDotDev/dump_hbcifs
Dump the Firmware
1. Similar to the previous post investigating the CIC Premium/High, the E89 spDaten pack was used, with the 9283251A.0pb extracted from the data\CM63F1 folder. I assumed the “CM” folder set was for the “CIC Mid” and this file was chosen as it was the only large file available in the folder with the same name as the “CIC” (63F1 series).
2. Unpack the 9283251A.0pb file.
An initial attempt to dump the 0pb file failed, as the base/boot part of the firmware does not contain the binary necessary to investigate the Navigation FSC activation. However, in the CIC High 0pb the file contained a standard IFS boot partition and an uncompressed ImageFS partition. The ImageFS partition was relatively easily dumped using a slightly modified version of the dumpifs tool. The new CIC Mid firmware uses a partition with an “hbcifs” signature, and there does not appear to be any tool to dump the “hbcifs” parition, or much information about hbcifs online.
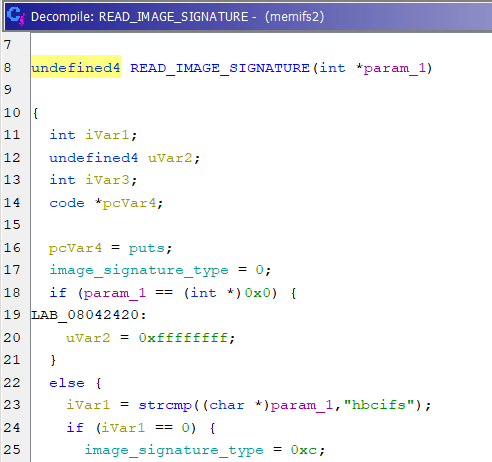
3. The limited information I was able to find on the internet (Post from “turbo-quattro” forum here) states that hbcifs stands for “Harmon/Becker Compresed IFS” and memifs2 is used to extract the hbcifs partition. This information appears to be correct as Harmon/Becker is the manufacturer of the CIC system. So we get the memifs2 binary from the CIC High 0pb, diassemble with Ghidra, and go to the main() Function.
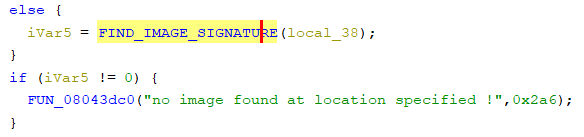
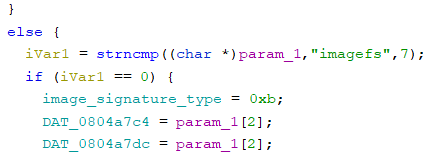
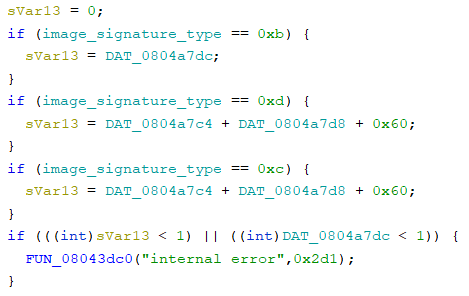
4. The first point of interest is the string “no image found at location specified”. Immediately preceding the statement we can see iVar5 being set. Following that function shows the subroutine which checks for the image signatures “hbcifs” and “imagefs”, and shows us which signature codes are used to identify the image type. We now know 0x0c is HBCIFS and 0x0b is ImageFS, so we can safely assume that 0x0d is IFS.
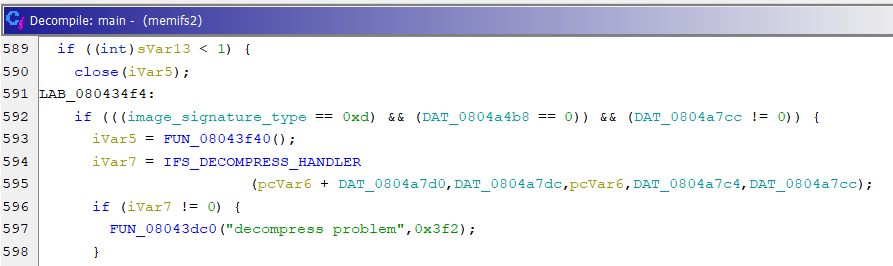
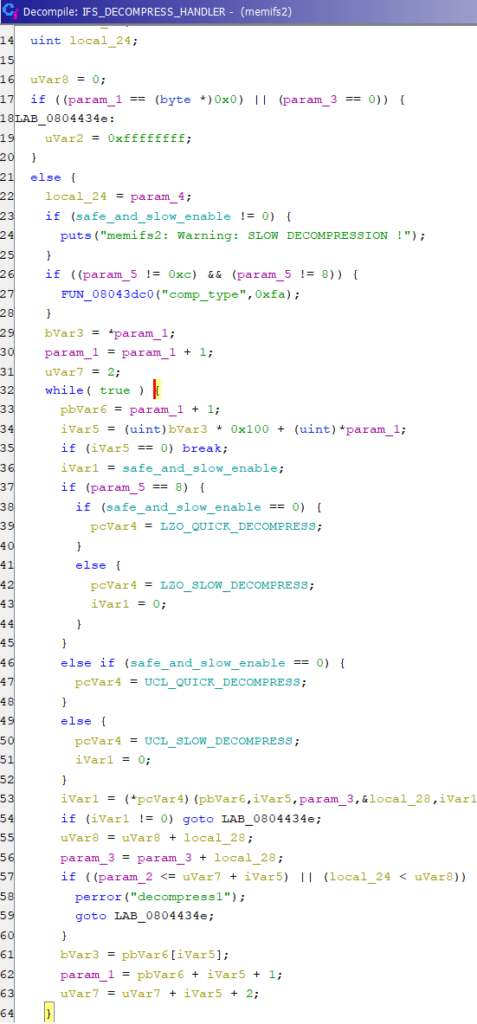
5. Scrolling further down the main() function shows a check for the IFS (0x0d) image signature as well as a statement indicating “decompress problem”. The function before the statement passes five (5) values and has decompression strings. Comparing the bit checks against the open source dumpifs struct, we can quickly determine the flags as well as the loop to decompress each block/buffer.
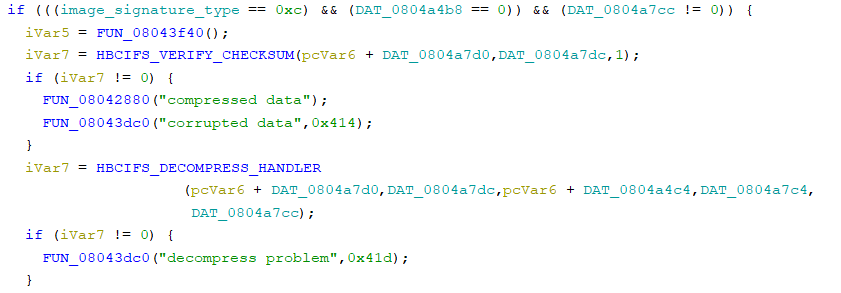
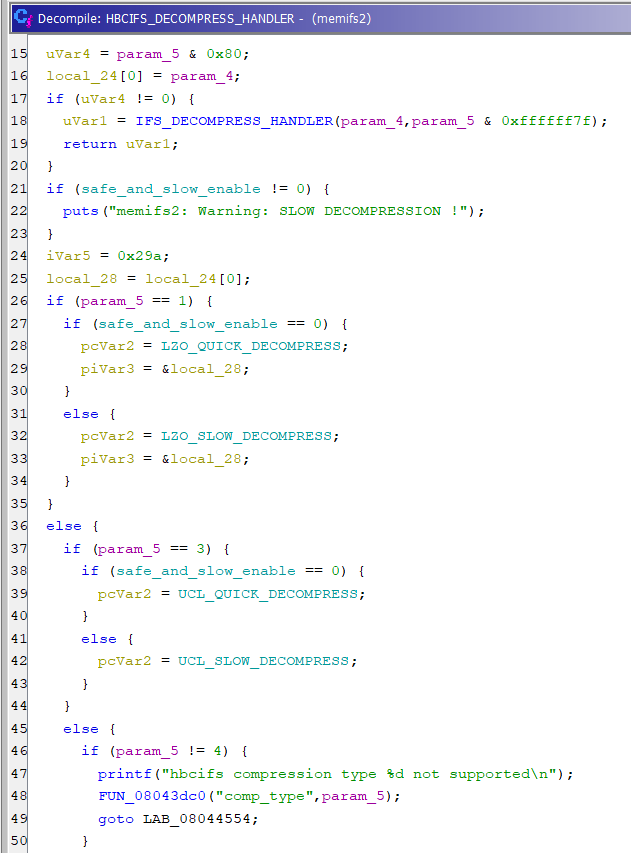
6. Returning to the main() function, and scrolling further down the disassembly, there is a check for the HBCIFS image signature (0x0c). Entering into the function above the “compressed data” string shows another string indicating a “crc16 int. error” and is likely a checksum routine prior to decompression. Below the “compressed data” and above the “decompress problem” string, the function passes a very similar five (5) values to the IFS Decompression Routine, but value three (3) is not identical. Entering into this function shows that it calls the IFS Decompression Routine, so the HBCIFS format is similar, but not identical to IFS decompression. Instead of decompressing multiple individual (up to) 64k blocks, HBCIFS passes the full size of the image to the LZO/UCL decompression. Additionally, unlike IFS, a different set of flags are used: 0x01 = LZO, 0x03 = UCL and 0x04 = {something else}
7. To decompress the HBCIFS, the dumpifs program can be modified to read the size from the HBCIFS header and pass it as a value to the IFS decompression routine.
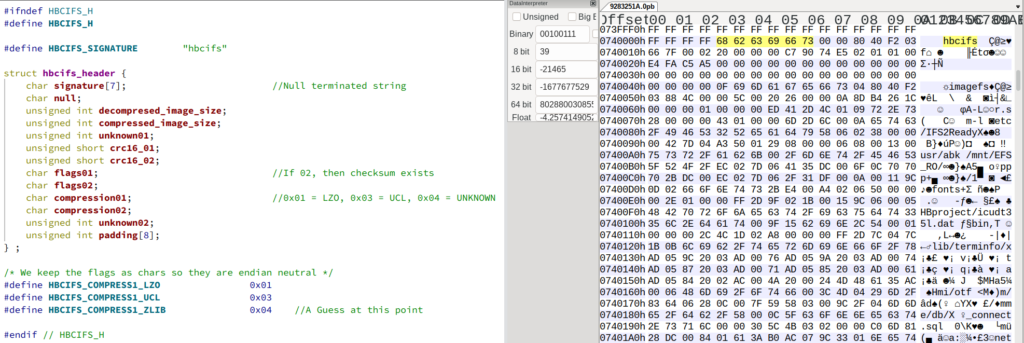
The structure for HBCIFS is therefore
struct {
char header[7] = "hbcifs"; //Null terminated string
char null;
unsigned int decompresed_image_size;
unsigned int compressed_image_size;
unsigned int unknown;
unsigned short crc16_01;
unsigned short crc16_02;
char flags[2]; //If 02, then checksum exists
char compression[2]; //0x01 = LZO, 0x03 = UCL, 0x04 = UNKNOWN
unsigned int unknown;
unsigned int padding[8];
} hbcifs;
hbcifs *hbcifs_hdr;
The Hex header in the 0pb file based against the above structure is:
68 62 63 69 66 73 00 char * "hbcifs" 00 char \0 80 40 F2 03 uint decompressed_image_size 66 7F 00 02 uint compressed_image_size 20 00 00 00 uint unknown C7 90 74 E5 crc16 checksums (compressed and decompressed) 02 01 if 0x02 then checksum exists, and add offsets 01 00 char flags. 01=LZO, 03=UCL, 04=? E4 FA C5 A5 more crc checksums? 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 uint padding[8] 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 0F char LZO_startbyte 69 6D 61 67 65 66 73 char * "imagefs"
8. Using the new tool on the CIC Premium/High (9283426A.0pb) and CIC Mid (9283251A.0pb) firmware allows us to dump all files from all firmware partitions without difficulty.
./dump_hbcifs 9283426A.0pb -d 928/ -x
Dump QNX IFS, ImageFS, and HBCIFS
********** Process IFS at: c0004
Image startup_size: 53512 (0xd108)
Image stored_size: 4831360 (0x49b880)
Compressed size: 4777844 (0x48e774)
LZO Decompress @0xcd10c
LZO Decompress rd=34191, wr=65536 @ 0xcd10c
LZO Decompress rd=37089, wr=65536 @ 0xd569d
LZO Decompress rd=39443, wr=65536 @ 0xde780
LZO Decompress rd=38684, wr=65536 @ 0xe8195
LZO Decompress rd=34541, wr=65536 @ 0xf18b3
LZO Decompress rd=39730, wr=65536 @ 0xf9fa2
LZO Decompress rd=21063, wr=65536 @ 0x103ad6
LZO Decompress rd=26539, wr=65536 @ 0x108d1f
LZO Decompress rd=29654, wr=65536 @ 0x10f4cc
LZO Decompress rd=34866, wr=65536 @ 0x1168a4
LZO Decompress rd=37119, wr=65536 @ 0x11f0d8
LZO Decompress rd=38623, wr=65536 @ 0x1281d9
LZO Decompress rd=38436, wr=65536 @ 0x1318ba
LZO Decompress rd=30973, wr=65536 @ 0x13aee0
LZO Decompress rd=33402, wr=65536 @ 0x1427df
LZO Decompress rd=29078, wr=65536 @ 0x14aa5b
LZO Decompress rd=25008, wr=65536 @ 0x151bf3
LZO Decompress rd=35614, wr=65536 @ 0x157da5
LZO Decompress rd=33787, wr=65536 @ 0x1608c5
LZO Decompress rd=27894, wr=65536 @ 0x168cc2
LZO Decompress rd=31540, wr=65536 @ 0x16f9ba
LZO Decompress rd=34096, wr=65536 @ 0x1774f0
LZO Decompress rd=34609, wr=65536 @ 0x17fa22
LZO Decompress rd=34996, wr=65536 @ 0x188155
LZO Decompress rd=36940, wr=65536 @ 0x190a0b
LZO Decompress rd=30603, wr=65536 @ 0x199a59
LZO Decompress rd=34517, wr=65536 @ 0x1a11e6
LZO Decompress rd=27137, wr=65536 @ 0x1a98bd
LZO Decompress rd=28288, wr=65536 @ 0x1b02c0
LZO Decompress rd=28062, wr=65536 @ 0x1b7142
LZO Decompress rd=24180, wr=65536 @ 0x1bdee2
LZO Decompress rd=22755, wr=65536 @ 0x1c3d58
LZO Decompress rd=31845, wr=65536 @ 0x1c963d
LZO Decompress rd=25593, wr=65536 @ 0x1d12a4
LZO Decompress rd=28792, wr=65536 @ 0x1d769f
LZO Decompress rd=25705, wr=65536 @ 0x1de719
LZO Decompress rd=31936, wr=65536 @ 0x1e4b84
LZO Decompress rd=36687, wr=65536 @ 0x1ec846
LZO Decompress rd=30143, wr=65536 @ 0x1f5797
LZO Decompress rd=35861, wr=65536 @ 0x1fcd58
LZO Decompress rd=32562, wr=65536 @ 0x20596f
LZO Decompress rd=33941, wr=65536 @ 0x20d8a3
LZO Decompress rd=36375, wr=65536 @ 0x215d3a
LZO Decompress rd=30788, wr=65536 @ 0x21eb53
LZO Decompress rd=31452, wr=65536 @ 0x226399
LZO Decompress rd=24186, wr=65536 @ 0x22de77
LZO Decompress rd=27349, wr=65536 @ 0x233cf3
LZO Decompress rd=34657, wr=65536 @ 0x23a7ca
LZO Decompress rd=32476, wr=65536 @ 0x242f2d
LZO Decompress rd=23773, wr=65536 @ 0x24ae0b
LZO Decompress rd=24554, wr=65536 @ 0x250aea
LZO Decompress rd=32214, wr=65536 @ 0x256ad6
LZO Decompress rd=22826, wr=65536 @ 0x25e8ae
LZO Decompress rd=26569, wr=65536 @ 0x2641da
LZO Decompress rd=36524, wr=65536 @ 0x26a9a5
LZO Decompress rd=30371, wr=65536 @ 0x273853
LZO Decompress rd=30032, wr=65536 @ 0x27aef8
LZO Decompress rd=31653, wr=65536 @ 0x28244a
LZO Decompress rd=31053, wr=65536 @ 0x289ff1
LZO Decompress rd=26868, wr=65536 @ 0x291940
LZO Decompress rd=26690, wr=65536 @ 0x298236
LZO Decompress rd=29253, wr=65536 @ 0x29ea7a
LZO Decompress rd=31816, wr=65536 @ 0x2a5cc1
LZO Decompress rd=30482, wr=65536 @ 0x2ad90b
LZO Decompress rd=29586, wr=65536 @ 0x2b501f
LZO Decompress rd=30184, wr=65536 @ 0x2bc3b3
LZO Decompress rd=24317, wr=65536 @ 0x2c399d
LZO Decompress rd=7963, wr=65536 @ 0x2c989c
LZO Decompress rd=23019, wr=65536 @ 0x2cb7b9
LZO Decompress rd=33355, wr=65536 @ 0x2d11a6
LZO Decompress rd=32615, wr=65536 @ 0x2d93f3
LZO Decompress rd=14152, wr=65536 @ 0x2e135c
LZO Decompress rd=26607, wr=65536 @ 0x2e4aa6
LZO Decompress rd=22020, wr=65536 @ 0x2eb297
LZO Decompress rd=41331, wr=65536 @ 0x2f089d
LZO Decompress rd=41988, wr=65536 @ 0x2faa12
LZO Decompress rd=22908, wr=65536 @ 0x304e18
LZO Decompress rd=26440, wr=65536 @ 0x30a796
LZO Decompress rd=30946, wr=65536 @ 0x310ee0
LZO Decompress rd=34331, wr=65536 @ 0x3187c4
LZO Decompress rd=31870, wr=65536 @ 0x320de1
LZO Decompress rd=33496, wr=65536 @ 0x328a61
LZO Decompress rd=31317, wr=65536 @ 0x330d3b
LZO Decompress rd=38921, wr=65536 @ 0x338792
LZO Decompress rd=31809, wr=65536 @ 0x341f9d
LZO Decompress rd=30516, wr=65536 @ 0x349be0
LZO Decompress rd=29491, wr=65536 @ 0x351316
LZO Decompress rd=30391, wr=65536 @ 0x35864b
LZO Decompress rd=30053, wr=65536 @ 0x35fd04
LZO Decompress rd=37739, wr=65536 @ 0x36726b
LZO Decompress rd=26696, wr=65536 @ 0x3705d8
LZO Decompress rd=35010, wr=65536 @ 0x376e22
LZO Decompress rd=33505, wr=65536 @ 0x37f6e6
LZO Decompress rd=23765, wr=65536 @ 0x3879c9
LZO Decompress rd=26712, wr=65536 @ 0x38d6a0
LZO Decompress rd=28912, wr=65536 @ 0x393efa
LZO Decompress rd=23474, wr=65536 @ 0x39afec
LZO Decompress rd=26334, wr=65536 @ 0x3a0ba0
LZO Decompress rd=29073, wr=65536 @ 0x3a7280
LZO Decompress rd=29408, wr=65536 @ 0x3ae413
LZO Decompress rd=26028, wr=65536 @ 0x3b56f5
LZO Decompress rd=30331, wr=65536 @ 0x3bbca3
LZO Decompress rd=31980, wr=65536 @ 0x3c3320
LZO Decompress rd=30478, wr=65536 @ 0x3cb00e
LZO Decompress rd=29217, wr=65536 @ 0x3d271e
LZO Decompress rd=28078, wr=65536 @ 0x3d9941
LZO Decompress rd=30841, wr=65536 @ 0x3e06f1
LZO Decompress rd=29650, wr=65536 @ 0x3e7f6c
LZO Decompress rd=27698, wr=65536 @ 0x3ef340
LZO Decompress rd=37530, wr=65536 @ 0x3f5f74
LZO Decompress rd=33058, wr=65536 @ 0x3ff210
LZO Decompress rd=23590, wr=65536 @ 0x407334
LZO Decompress rd=24296, wr=65536 @ 0x40cf5c
LZO Decompress rd=30123, wr=65536 @ 0x412e46
LZO Decompress rd=23156, wr=65536 @ 0x41a3f3
LZO Decompress rd=34181, wr=65536 @ 0x41fe69
LZO Decompress rd=22852, wr=65536 @ 0x4283f0
LZO Decompress rd=24467, wr=65536 @ 0x42dd36
LZO Decompress rd=33145, wr=65536 @ 0x433ccb
LZO Decompress rd=19274, wr=65536 @ 0x43be46
LZO Decompress rd=19516, wr=65536 @ 0x440992
LZO Decompress rd=19284, wr=65536 @ 0x4455d0
LZO Decompress rd=18282, wr=65536 @ 0x44a126
LZO Decompress rd=32923, wr=65536 @ 0x44e892
LZO Decompress rd=26190, wr=65536 @ 0x45692f
LZO Decompress rd=31550, wr=65536 @ 0x45cf7f
LZO Decompress rd=22450, wr=65536 @ 0x464abf
LZO Decompress rd=27507, wr=65536 @ 0x46a273
LZO Decompress rd=22980, wr=65536 @ 0x470de8
LZO Decompress rd=33620, wr=65536 @ 0x4767ae
LZO Decompress rd=21620, wr=65536 @ 0x47eb04
LZO Decompress rd=15229, wr=65536 @ 0x483f7a
LZO Decompress rd=13205, wr=65536 @ 0x487af9
LZO Decompress rd=16721, wr=65536 @ 0x48ae90
LZO Decompress rd=23371, wr=65536 @ 0x48efe3
LZO Decompress rd=21596, wr=65536 @ 0x494b30
LZO Decompress rd=11584, wr=65536 @ 0x499f8e
LZO Decompress rd=18337, wr=65536 @ 0x49ccd0
LZO Decompress rd=19544, wr=65536 @ 0x4a1473
LZO Decompress rd=18649, wr=65536 @ 0x4a60cd
LZO Decompress rd=22816, wr=65536 @ 0x4aa9a8
LZO Decompress rd=23245, wr=65536 @ 0x4b02ca
LZO Decompress rd=25023, wr=65536 @ 0x4b5d99
LZO Decompress rd=16764, wr=65536 @ 0x4bbf5a
LZO Decompress rd=16908, wr=65536 @ 0x4c00d8
LZO Decompress rd=25975, wr=65536 @ 0x4c42e6
LZO Decompress rd=11323, wr=65536 @ 0x4ca85f
LZO Decompress rd=357, wr=65536 @ 0x4cd49c
LZO Decompress rd=357, wr=65536 @ 0x4cd603
LZO Decompress rd=357, wr=65536 @ 0x4cd76a
LZO Decompress rd=4775, wr=65536 @ 0x4cd8d1
LZO Decompress rd=34167, wr=65536 @ 0x4ceb7a
LZO Decompress rd=34514, wr=65536 @ 0x4d70f3
LZO Decompress rd=28379, wr=65536 @ 0x4df7c7
LZO Decompress rd=33636, wr=65536 @ 0x4e66a4
LZO Decompress rd=65175, wr=65536 @ 0x4eea0a
LZO Decompress rd=61672, wr=61440 @ 0x4fe8a3
LZO Decompress rd=4117, wr=4096 @ 0x50d98d
LZO Decompress rd=61676, wr=61440 @ 0x50e9a4
LZO Decompress rd=4117, wr=4096 @ 0x51da92
LZO Decompress rd=61676, wr=61440 @ 0x51eaa9
LZO Decompress rd=4118, wr=4096 @ 0x52db97
LZO Decompress rd=61682, wr=61440 @ 0x52ebaf
LZO Decompress rd=4116, wr=4096 @ 0x53dca3
LZO Decompress rd=61678, wr=61440 @ 0x53ecb9
LZO Decompress rd=4117, wr=4096 @ 0x54dda9
LZO Decompress rd=32077, wr=65536 @ 0x54edc0
LZO Decompress rd=2307, wr=65536 @ 0x556b0f
LZO Decompress rd=4163, wr=65536 @ 0x557414
LZO Decompress rd=5273, wr=65536 @ 0x558459
LZO Decompress rd=8071, wr=19532 @ 0x5598f4
Decompressed 4777499 bytes-> 10832972 bytes
etc/system/config/display_wide.conf ... size 260
etc/L6Version.txt ... size 10
proc/boot/procnto-instr ... size 413696
usr/bin/pidin ... size 58060
proc/boot/.script ... size 2980
usr/share/wave/PDCBeepRearStart.wav ... size 352
etc/shells ... size 26
bin/sloginfo ... size 10011
etc/videoctrl-L6.cfg ... size 1995
etc/system/config/display_special.conf ... size 260
proc/boot/libc.so.2 ... size 421888
proc/boot/devc-sersci ... size 62492
etc/inetd.conf ... size 2726
etc/passwd ... size 312
lib/libecpp-ne.so.4 ... size 114688
lib/dll/devg-carmine.so ... size 175788
etc/system/config/display_narrow.conf ... size 258
bin/checkpersistency.sh ... size 82
lib/dll/libGLES_CM.so.1 ... size 130739
etc/system/config/img.conf ... size 243
etc/shadow ... size 69
lib/dll/img_codec_png.so ... size 140859
usr/share/wave/PDCBeepLoop.wav ... size 1808
bin/createHBpersistence.sh ... size 608
etc/ftpusers ... size 67
lib/libsocket.so.2 ... size 139264
usr/lib/libgf.so.1 ... size 103677
usr/share/wave/PDCBeepRearLoop.wav ... size 1808
etc/system/config/carmine-l6-7534-1280x480.conf ... size 962
usr/lib/libimg.so.1 ... size 72780
usr/share/wave/PDCBeepEnd.wav ... size 946
lib/libasound.so.2 ... size 95805
etc/system/config/carmine-l6-7534-800x480hb.conf ... size 959
etc/system/config/carmine-l6-7534-800x480.conf ... size 957
proc/boot/server.cfg ... size 548
lib/libm.so.2 ... size 132543
usr/share/wave/PDCBeepRearEnd.wav ... size 942
etc/profile ... size 595
proc/boot/pci-l6_B001.cfg ... size 349
usr/share/wave/PDCBeepStart.wav ... size 342
etc/layermanager.cfg ... size 203
etc/videowatchdog-L6.cfg ... size 180
usr/lib/libffb.so.2 ... size 76862
etc/hosts ... size 118
usr/lib/libmhpfilter.so.1 ... size 12288
lib/dll/deva-ctrl-hb_fpga.so ... size 46694
lib/libcam.so.2 ... size 78078
usr/share/wave/PDCBeep.wav ... size 3604
usr/lib/cam-cdrom.so ... size 22441
usr/lib/cam-disk.so ... size 13223
usr/lib/fs-qnx4.so ... size 56983
usr/lib/fs-qnx6.so ... size 71923
usr/lib/fs-cd.so ... size 50552
usr/lib/fs-dos.so ... size 81336
usr/lib/fs-udf.so ... size 73690
usr/lib/io-blk.so ... size 158141
lib/dll/dspipc-dra300.so ... size 86016
lib/libbacktrace.so.1 ... size 22777
bin/waitfor ... size 22430
bin/mkdir ... size 10403
bin/cp ... size 35556
bin/slay ... size 17384
sbin/devf-generic ... size 200104
usr/sbin/tracelogger ... size 18495
usr/bin/on ... size 22430
usr/bin/flashctl ... size 15794
bin/dev-dspipc ... size 81505
bin/fesh ... size 22205
usr/bin/nice ... size 7566
bin/if-test ... size 18662
usr/bin/memifs2 ... size 45056
usr/bin/slogger ... size 16384
usr/bin/pci-sh7785 ... size 81920
usr/bin/dev-sysregs ... size 65536
sbin/io-display ... size 46132
sbin/io-audio ... size 136336
usr/bin/dev-ipc ... size 69632
usr/bin/dev-videoctrl ... size 49152
usr/bin/dev-mlb ... size 73728
usr/bin/dev-ssi-hbfpga ... size 40960
usr/bin/dev-videowatchdog ... size 40960
usr/bin/dev-spi-hbfpga ... size 69632
usr/bin/devb-eide-hbfpga ... size 121751
usr/bin/vdev-eeprom ... size 139264
usr/bin/vdev-tunnelipc ... size 32768
usr/bin/layermanager ... size 237568
usr/bin/dev-mv2trace ... size 106496
usr/bin/srv-starter-QNX ... size 180224
usr/HBproject/CicHighAsnRoot ... size 4861952
bin/ksh ... size 178307
bin/echo ... size 7423
usr/bin/devc-ser8250hb ... size 82833
etc/splash_wide.png ... size 245617
etc/splash_narrow.png ... size 177297
etc/sysregs-l6-7534.cfg ... size 151142
etc/starter.cfg ... size 85933
etc/termcap ... size 6749
etc/lbt ... size 3908
usr/share/wave/PDCBeepRear.wav ... size 3592
Image startup_size: 53512 (0xd108)
Image stored_size: 4831360 (0x49b880)
Compressed size: 4777844 (0x48e774)
********** Continue search at: 55b884
********** Process ImageFS at: 580004
usr/lib/terminfo/q/qansi-g ... size 2092
usr/Hmi/otf/start_otf.sh ... size 68
usr/bin/inetd ... size 45056
sbin/devc-pty ... size 53248
sbin/mqueue ... size 20480
sbin/io-usb ... size 122923
etc/config/umass-enum-en5-in-car.cfg ... size 3767
usr/bin/check_metrics.sh ... size 262
usr/bin/vdev-medialaunch ... size 102400
usr/bin/proc_scriptlauncher ... size 16384
usr/bin/mme-update ... size 57344
usr/bin/dev-nvram ... size 32768
lib/dll/img_codec_jpg.so ... size 105962
etc/fstab ... size 529
usr/lib/mme-imgprc-gf.so ... size 16384
sbin/io-net ... size 77710
usr/bin/cleanEntertainment.sh ... size 109
sbin/pipe ... size 24576
lib/dll/nfm-autoip.so ... size 20531
etc/config/umass-enum-en5-private.cfg ... size 3711
usr/bin/HUShutdown.sh ... size 331
usr/HBproject/CicHighAsnSecond ... size 11124736
usr/bin/vdev-flexgps ... size 278528
usr/bin/ndr ... size 593920
usr/bin/usbPowerMonitor ... size 32768
usr/bin/multicored ... size 217088
usr/bin/srv_drivehandler ... size 335872
sbin/mcd ... size 45056
usr/sbin/io-media-margi ... size 270336
usr/sbin/srv-dvdplayer ... size 671744
usr/sbin/gracenote_srvr ... size 385024
lib/dll/mdp-gracenote_client.so ... size 20480
usr/sbin/srv-mmelauncher ... size 45056
usr/Hmi/otf/BMWOTFagent ... size 32768
usr/Hmi/otf/libBMWOTFapi.so.1 ... size 32768
usr/Hmi/otf/libBMWOTFapi.so.2 ... size 28672
usr/Hmi/otf/libBMWOTFapi.so.3 ... size 28672
usr/Hmi/otf/libBMWOTFdrvMCD.so.1 ... size 16384
usr/Hmi/otf/libBMWOTFdrvSerial.so.1 ... size 20480
usr/Hmi/otf/libBMWOTFdrvSocket.so.1 ... size 12288
usr/Hmi/bin/HmiMain ... size 19685376
usr/bin/dumper ... size 24103
etc/fstab_qnx4 ... size 414
etc/qkcp_export.cfg ... size 50
usr/bin/pidinbt ... size 53810
etc/pre_starting_qdb.sh ... size 3517
usr/sbin/sqlite_console ... size 48641
usr/bin/createQDBPaths.sh ... size 490
usr/sbin/mme ... size 1261569
etc/mcd.conf ... size 3612
etc/ecddb.ka ... size 256
usr/Hmi/otf/socket.cfg ... size 126
etc/qkcp_import.cfg ... size 50
etc/mme.label ... size 37
usr/sbin/qdb ... size 128425
etc/mmelauncher.cfg ... size 2597
etc/ftpd.conf ... size 36
usr/bin/dhcp.client ... size 64676
usr/mme/db/mme_connect.sql ... size 856
usr/bin/fs-nfs3 ... size 81698
etc/post_starting_qdb.sh ... size 102
usr/bin/gunzip ... size 58262
etc/config/GPSairborne_L6.cfg ... size 3037
bin/flashit ... size 13707
etc/hddmgr_qnx4.conf ... size 2521
bin/hostname ... size 6832
etc/ipnat.conf ... size 1293
bin/qconn ... size 130053
etc/hfs.cfg ... size 1006
bin/uue ... size 8776
etc/ipod.cfg ... size 3441
bin/cat ... size 7955
bin/mv ... size 10960
etc/mmelauncher_upgrade_mme_10.sh ... size 1241
sbin/ifconfig ... size 37411
usr/bin/runDumper.sh ... size 2894
usr/bin/runPidin.sh ... size 639
lib/dll/devu-ehci.so ... size 36253
etc/ipf.conf ... size 553
lib/dll/devu-ohci.so ... size 29545
usr/mme/db/qdb.cfg ... size 2759
sbin/devb-umass ... size 30716
usr/lib/terminfo/v/vt102-plus ... size 1987
sbin/devc-serusb_prolific ... size 79044
etc/hddmgr.conf ... size 2751
lib/dll/devn-asix.so ... size 73046
lib/dll/devn-micrel8841.so ... size 58018
usr/lib/terminfo/v/vs100 ... size 2384
usr/lib/terminfo/v/vi200-f ... size 1035
lib/dll/npm-qnet-l4_lite.so ... size 188416
lib/dll/devn-mlb.so ... size 73728
usr/bin/HBSerDev ... size 72736
usr/lib/terminfo/v/viewpoint ... size 972
bin/mount ... size 15965
bin/umount ... size 6707
usr/lib/terminfo/q/qnx2 ... size 1460
bin/login ... size 20657
usr/lib/terminfo/x/xterm ... size 2384
usr/lib/terminfo/q/qnx ... size 1491
usr/bin/rm ... size 10380
etc/mmelauncher_upgrade_mme_29.sh ... size 1862
bin/gzip ... size 58262
usr/lib/terminfo/q/qansi-m ... size 2357
etc/dotMmeDotDelete.sh ... size 813
usr/sbin/telnetd ... size 125940
usr/lib/terminfo/v/visual ... size 1035
usr/sbin/ftpd ... size 94542
usr/lib/terminfo/q/qansi-w ... size 2357
etc/mmelauncher_upgrade_mme_custom_3.sh ... size 1398
usr/sbin/if_up ... size 7981
usr/lib/libexpat.so.2 ... size 77072
usr/sbin/pppd ... size 185568
usr/lib/terminfo/q/qansi-t ... size 2301
sbin/sysctl ... size 19604
etc/mmelauncher_upgrade_mme_28.sh ... size 845
sbin/route ... size 29410
usr/lib/terminfo/q/qansi ... size 2295
usr/lib/terminfo/q/qvt101 ... size 1048
lib/dll/npm-tcpip-v4.so ... size 355185
usr/lib/terminfo/q/qvt108 ... size 1048
lib/dll/npm-pppmgr.so ... size 94082
usr/lib/libsac.so ... size 8192
usr/lib/libpal_core.so ... size 57344
usr/lib/libparsercreator.so ... size 32768
usr/lib/libpdiparser.so ... size 118784
lib/dll/lsm-ipfilter-v4.so ... size 98304
usr/sbin/ipf ... size 39049
usr/lib/terminfo/q/qnxm ... size 1758
usr/sbin/ipnat ... size 33486
usr/lib/terminfo/x/xterm-q ... size 2294
etc/mmelauncher_upgrade_mme_custom_16.sh ... size 1034
usr/bin/vdev-fsys-dbc ... size 29502
usr/lib/terminfo/t/test ... size 1984
etc/mmelauncher_upgrade_mme_11.sh ... size 1241
usr/sbin/io-fs ... size 136631
usr/lib/terminfo/x/xterm-m ... size 1930
sbin/chkqnx6fs ... size 32442
sbin/chkfsys ... size 38008
usr/lib/terminfo/v/vs100s ... size 1913
etc/mmelauncher_upgrade_mme_custom_17.sh ... size 1034
usr/bin/touch ... size 9190
usr/lib/terminfo/x/xterms ... size 1913
usr/lib/terminfo/a/ansi ... size 1179
bin/sync ... size 6037
usr/lib/terminfo/q/qnxw ... size 1748
lib/libecpp-ne.so.3 ... size 86016
lib/libcpp.so.3 ... size 434176
usr/lib/libproject_qnxapp_collect_srvlayermanager_client.so ... size 24576
lib/libusbdi.so.2 ... size 48079
usr/lib/terminfo/q/qvt102 ... size 1033
lib/dll/libfont.so.1 ... size 53248
usr/lib/libFF-T2K-cache.so.2 ... size 9693
usr/lib/terminfo/q/qnxtmono ... size 1707
etc/mmelauncher_upgrade_mme_library_8.sh ... size 798
usr/lib/libFF-T2K-fm.so.1 ... size 14087
usr/lib/terminfo/v/vt102 ... size 1703
usr/lib/libFF-T2K.so.2 ... size 262775
usr/lib/terminfo/v/vt102-am ... size 1703
usr/lib/terminfo/q/qnxt ... size 1686
usr/lib/libz.so.2 ... size 69915
usr/lib/terminfo/q/qnxt4 ... size 1686
usr/mme/db/mme_custom.sql ... size 1661
lib/dll/libhiddi.so.1 ... size 40960
usr/lib/libpal_audio.so ... size 20480
usr/lib/libpal_bt.so ... size 28672
usr/lib/libscp_core.so ... size 176128
usr/lib/libsse.so ... size 278528
usr/lib/libsvox.so ... size 741376
usr/lib/libtools.so ... size 626688
usr/lib/libaliveservice.so ... size 16384
usr/lib/libaudiocoder.so ... size 16384
usr/lib/libaudiocoder_ans.so ... size 20480
usr/lib/libaudiocoder_tts.so ... size 61440
usr/lib/libaudiomatrixservice.so ... size 81920
usr/lib/libdsr.so ... size 405504
usr/lib/libhostagent.so ... size 20480
usr/lib/libmonitorservice.so ... size 73728
usr/lib/libprompterservice.so ... size 225280
usr/lib/librecognitionservice.so ... size 266240
usr/lib/librmssservice.so ... size 40960
usr/lib/libsaipservice.so ... size 90112
usr/lib/libsaopservice.so ... size 53248
usr/lib/libscfservice.so ... size 90112
usr/lib/libspellmatcherservice.so ... size 229376
usr/lib/libsss_config.so ... size 8192
usr/lib/libtnservice.so ... size 151552
usr/lib/libunidb_sqlite3so.so ... size 24576
usr/lib/libhbsystime_posix_1_0.so ... size 8192
lib/dll/dspipc-dm642.so ... size 69632
lib/libdspipc.so ... size 24576
usr/lib/libmldr.so ... size 49152
usr/bin/srv-hddmgr ... size 68552
etc/mmelauncher_upgrade_mme_custom_10.sh ... size 1030
bin/inflator ... size 21830
etc/mmelauncher_upgrade_mme_custom_27.sh ... size 1598
etc/mmelauncher_upgrade_mme_custom_11.sh ... size 1030
usr/lib/fs-nt.so ... size 40241
usr/lib/libsqlite3.so.1 ... size 471040
usr/lib/libthirdparty_qdb_icu_3_5_bmw.so ... size 24576
usr/lib/libthirdparty_icu_3_5_bmw.so ... size 1191936
usr/lib/libasiacollation.so ... size 53248
usr/bin/qdblauncher ... size 18428
usr/lib/terminfo/q/qnx4 ... size 1491
usr/lib/libmmfilter.so.1 ... size 16384
usr/lib/libmmedia.so.1 ... size 45056
usr/lib/libaoi.so.1 ... size 16384
usr/lib/libmme.so.1 ... size 45056
usr/lib/libqdb.so.1 ... size 32768
usr/lib/libxml2.so.1 ... size 602112
lib/dll/mmedia/aac_parser.so ... size 57344
lib/dll/mmedia/cdda_parser.so ... size 20480
lib/dll/mmedia/cdda_streamer.so ... size 20480
lib/dll/mmedia/fildes_streamer.so ... size 16384
lib/dll/mmedia/media_streamer.so ... size 20480
lib/dll/mmedia/mmipc_writer.so ... size 61440
lib/dll/mmedia/mpega_parser.so ... size 61440
lib/dll/mmedia/mp4_parser.so ... size 94208
lib/dll/mmedia/queue_filter.so ... size 16384
lib/dll/mmedia/stream_reader.so ... size 20480
lib/dll/mmedia/wma9_parser.so ... size 274432
usr/sbin/mmecli ... size 193189
usr/lib/terminfo/q/qnxs2 ... size 1460
usr/lib/terminfo/v/vt100 ... size 1388
usr/sbin/qdbc ... size 34062
usr/lib/terminfo/v/vt100-am ... size 1388
etc/mmelauncher_upgrade_mme_custom_2.sh ... size 1385
usr/sbin/fileset ... size 22902
usr/lib/terminfo/q/qnxt2 ... size 1371
lib/dll/mmedia/dvd_eventer.so ... size 36864
lib/dll/mmedia/mmipc_encoder.so ... size 81920
lib/dll/mmedia/muxer.so ... size 57344
lib/dll/mmedia/parser_dvd.so ... size 28672
lib/dll/mmedia/parser_mpgvfile.so ... size 45056
lib/dll/mmedia/parser_vcd.so ... size 32768
lib/dll/mmedia/rawfile_writer.so ... size 20480
lib/dll/mmedia/reader_dvd.so ... size 32768
lib/dll/mmedia/streamer_dvd.so ... size 40960
lib/dll/mmedia/tmpfile_streamer.so ... size 16384
lib/dll/mmedia/wms_control.so ... size 20480
lib/dll/mmedia/wms_streamer.so ... size 12288
lib/dll/mmedia/writer_dm642.so ... size 43581
etc/mmelauncher_upgrade_mme_12.sh ... size 1241
lib/dll/mmedia/dvd_eventer.so ... size 36864
lib/dll/mmedia/dmb_parser.so ... size 79423
etc/mmelauncher_upgrade_mme_13.sh ... size 1241
etc/mmelauncher_upgrade_mme_14.sh ... size 1241
lib/dll/mmedia/dmb_streamer.so ... size 12288
lib/dll/libAppFramework.A.so ... size 69632
lib/dll/libCoreFramework.A.so ... size 122880
lib/dll/libhmibidi.so ... size 77824
lib/dll/libcpp.so.4 ... size 466944
usr/bin/apnl6 ... size 28212
usr/bin/apnnav ... size 9570916
etc/mmelauncher_upgrade_mme_15.sh ... size 1241
usr/bin/VssServer ... size 31980
usr/lib/libcpp-ne.so.4 ... size 368640
lib/dll/libbmwqkcp.so.1 ... size 8192
usr/bin/scp ... size 40960
etc/mmelauncher_upgrade_mme_22.sh ... size 36366
etc/mme.conf ... size 35048
etc/mmelauncher_upgrade_mme_library_6.sh ... size 34435
etc/sss/ar_XA/default.cfg ... size 33888
etc/sss/de_DE/default.cfg ... size 33888
etc/sss/el_GR/default.cfg ... size 33888
etc/sss/en_GB/default.cfg ... size 33888
etc/sss/en_US/default.cfg ... size 33888
etc/sss/fr_FR/default.cfg ... size 33888
etc/sss/es_ES/default.cfg ... size 33888
etc/sss/hu_HU/default.cfg ... size 33888
etc/sss/it_IT/default.cfg ... size 33888
etc/sss/nl_NL/default.cfg ... size 33888
etc/sss/pl_PL/default.cfg ... size 33888
etc/sss/pt_PT/default.cfg ... size 33888
etc/sss/ru_RU/default.cfg ... size 33888
etc/sss/sv_SE/default.cfg ... size 33888
etc/sss/tr_TR/default.cfg ... size 33888
etc/sss/ja_JP/default.cfg ... size 33888
etc/sss/ko_KR/default.cfg ... size 33888
etc/sss/en_RR/default.cfg ... size 32851
usr/mme/db/mme.sql ... size 32134
usr/mme/db/mme_library.sql ... size 12084
etc/io-media-margi.cfg ... size 9074
usr/mme/db/mme_data.sql ... size 7928
etc/mmelauncher_upgrade_mme_custom_26.sh ... size 6784
usr/mme/db/mme_mp3_speech.sql ... size 6540
usr/mme/db/mme_temp.sql ... size 4337
etc/mmelauncher_upgrade_mme_16.sh ... size 1241
etc/mmelauncher_upgrade_mme_17.sh ... size 1241
etc/mmelauncher_upgrade_mme_18.sh ... size 1241
etc/mmelauncher_upgrade_mme_19.sh ... size 1241
etc/mmelauncher_upgrade_mme_20.sh ... size 1241
etc/mmelauncher_upgrade_mme_21.sh ... size 1241
etc/mmelauncher_upgrade_mme_23.sh ... size 1241
etc/mmelauncher_upgrade_mme_24.sh ... size 1241
etc/mmelauncher_upgrade_mme_25.sh ... size 1241
etc/mmelauncher_upgrade_mme_26.sh ... size 1241
etc/mmelauncher_upgrade_mme_27.sh ... size 1241
etc/mmelauncher_upgrade_mme_0.sh ... size 1238
etc/mmelauncher_upgrade_mme_1.sh ... size 1238
etc/mmelauncher_upgrade_mme_2.sh ... size 1238
etc/mmelauncher_upgrade_mme_3.sh ... size 1238
etc/mmelauncher_upgrade_mme_4.sh ... size 1238
etc/mmelauncher_upgrade_mme_5.sh ... size 1238
etc/mmelauncher_upgrade_mme_6.sh ... size 1238
etc/mmelauncher_upgrade_mme_7.sh ... size 1238
etc/mmelauncher_upgrade_mme_8.sh ... size 1238
etc/mmelauncher_upgrade_mme_9.sh ... size 1238
etc/mmelauncher_upgrade_mme_custom_12.sh ... size 1030
etc/mmelauncher_upgrade_mme_custom_13.sh ... size 1030
etc/mmelauncher_upgrade_mme_custom_14.sh ... size 1030
etc/mmelauncher_upgrade_mme_custom_15.sh ... size 1030
etc/mmelauncher_upgrade_mme_custom_19.sh ... size 1030
etc/mmelauncher_upgrade_mme_custom_20.sh ... size 1030
etc/mmelauncher_upgrade_mme_custom_21.sh ... size 1030
etc/mmelauncher_upgrade_mme_custom_22.sh ... size 1030
etc/mmelauncher_upgrade_mme_custom_23.sh ... size 1030
etc/mmelauncher_upgrade_mme_custom_24.sh ... size 1030
etc/mmelauncher_upgrade_mme_custom_25.sh ... size 1030
etc/mmelauncher_upgrade_mme_custom_18.sh ... size 1027
etc/mmelauncher_upgrade_mme_custom_4.sh ... size 1025
etc/mmelauncher_upgrade_mme_custom_5.sh ... size 1025
etc/mmelauncher_upgrade_mme_custom_6.sh ... size 1025
etc/mmelauncher_upgrade_mme_custom_7.sh ... size 1025
etc/mmelauncher_upgrade_mme_custom_8.sh ... size 1025
etc/mmelauncher_upgrade_mme_custom_9.sh ... size 1025
etc/mmelauncher_upgrade_mme_library_0.sh ... size 956
etc/mmelauncher_upgrade_mme_library_1.sh ... size 956
etc/mmelauncher_upgrade_mme_library_2.sh ... size 956
etc/mmelauncher_upgrade_mme_library_3.sh ... size 956
etc/mmelauncher_upgrade_mme_library_4.sh ... size 956
etc/mmelauncher_upgrade_mme_library_5.sh ... size 956
etc/mmelauncher_upgrade_mme_library_7.sh ... size 956
etc/mmelauncher_upgrade_mme_custom_0.sh ... size 950
etc/mmelauncher_upgrade_mme_custom_1.sh ... size 950
usr/lib/terminfo/v/vt52 ... size 905
********** Continue search at: 3e83f68
********** Process IFS at: 45f5854
dump_hbcifs: Zero check failed, not a valid IFS header. Continuing search
dump_hbcifs: Unable to find startup header in 9283426A.0pb
********** Continue search at: 45f5855
Nothing left to extract from 9283426A.0pb
./dump_hbcifs 9283251A.0pb -d 9283251A/ -x
Dump QNX IFS, ImageFS, and HBCIFS
********** Process IFS at: 180004
Image startup_size: 53512 (0xd108)
Image stored_size: 5894240 (0x59f060)
Compressed size: 5840724 (0x591f54)
LZO Decompress @0x18d10c
LZO Decompress rd=35312, wr=65536 @ 0x18d10c
LZO Decompress rd=36973, wr=65536 @ 0x195afe
LZO Decompress rd=39243, wr=65536 @ 0x19eb6d
LZO Decompress rd=39876, wr=65536 @ 0x1a84ba
LZO Decompress rd=33011, wr=65536 @ 0x1b2080
LZO Decompress rd=40450, wr=65536 @ 0x1ba175
LZO Decompress rd=21168, wr=65536 @ 0x1c3f79
LZO Decompress rd=26679, wr=65536 @ 0x1c922b
LZO Decompress rd=29459, wr=65536 @ 0x1cfa64
LZO Decompress rd=35156, wr=65536 @ 0x1d6d79
LZO Decompress rd=36829, wr=65536 @ 0x1df6cf
LZO Decompress rd=39282, wr=65536 @ 0x1e86ae
LZO Decompress rd=37236, wr=65536 @ 0x1f2022
LZO Decompress rd=33619, wr=65536 @ 0x1fb198
LZO Decompress rd=32088, wr=65536 @ 0x2034ed
LZO Decompress rd=28141, wr=65536 @ 0x20b247
LZO Decompress rd=25587, wr=65536 @ 0x212036
LZO Decompress rd=41779, wr=65536 @ 0x21842b
LZO Decompress rd=32243, wr=65536 @ 0x222760
LZO Decompress rd=31540, wr=65536 @ 0x22a555
LZO Decompress rd=34013, wr=65536 @ 0x23208b
LZO Decompress rd=34609, wr=65536 @ 0x23a56a
LZO Decompress rd=34959, wr=65536 @ 0x242c9d
LZO Decompress rd=36940, wr=65536 @ 0x24b52e
LZO Decompress rd=30603, wr=65536 @ 0x25457c
LZO Decompress rd=34517, wr=65536 @ 0x25bd09
LZO Decompress rd=26797, wr=65536 @ 0x2643e0
LZO Decompress rd=28289, wr=65536 @ 0x26ac8f
LZO Decompress rd=28645, wr=65536 @ 0x271b12
LZO Decompress rd=24180, wr=65536 @ 0x278af9
LZO Decompress rd=22755, wr=65536 @ 0x27e96f
LZO Decompress rd=31341, wr=65536 @ 0x284254
LZO Decompress rd=26051, wr=65536 @ 0x28bcc3
LZO Decompress rd=28792, wr=65536 @ 0x292288
LZO Decompress rd=25832, wr=65536 @ 0x299302
LZO Decompress rd=34817, wr=65536 @ 0x29f7ec
LZO Decompress rd=30210, wr=65536 @ 0x2a7fef
LZO Decompress rd=37705, wr=65536 @ 0x2af5f3
LZO Decompress rd=30353, wr=65536 @ 0x2b893e
LZO Decompress rd=33500, wr=65536 @ 0x2bffd1
LZO Decompress rd=36547, wr=65536 @ 0x2c82af
LZO Decompress rd=31221, wr=65536 @ 0x2d1174
LZO Decompress rd=34872, wr=65536 @ 0x2d8b6b
LZO Decompress rd=24567, wr=65536 @ 0x2e13a5
LZO Decompress rd=24802, wr=65536 @ 0x2e739e
LZO Decompress rd=34458, wr=65536 @ 0x2ed482
LZO Decompress rd=32618, wr=65536 @ 0x2f5b1e
LZO Decompress rd=22470, wr=65536 @ 0x2fda8a
LZO Decompress rd=25687, wr=65536 @ 0x303252
LZO Decompress rd=30482, wr=65536 @ 0x3096ab
LZO Decompress rd=25209, wr=65536 @ 0x310dbf
LZO Decompress rd=28482, wr=65536 @ 0x31703a
LZO Decompress rd=31899, wr=65536 @ 0x31df7e
LZO Decompress rd=32008, wr=65536 @ 0x325c1b
LZO Decompress rd=31199, wr=65536 @ 0x32d925
LZO Decompress rd=29864, wr=65536 @ 0x335306
LZO Decompress rd=33639, wr=65536 @ 0x33c7b0
LZO Decompress rd=28711, wr=65536 @ 0x344b19
LZO Decompress rd=28301, wr=65536 @ 0x34bb42
LZO Decompress rd=27171, wr=65536 @ 0x3529d1
LZO Decompress rd=25156, wr=65536 @ 0x3593f6
LZO Decompress rd=30500, wr=65536 @ 0x35f63c
LZO Decompress rd=30151, wr=65536 @ 0x366d62
LZO Decompress rd=17358, wr=65536 @ 0x36e32b
LZO Decompress rd=11815, wr=65536 @ 0x3726fb
LZO Decompress rd=29114, wr=65536 @ 0x375524
LZO Decompress rd=35360, wr=65536 @ 0x37c6e0
LZO Decompress rd=23186, wr=65536 @ 0x385102
LZO Decompress rd=12502, wr=65536 @ 0x38ab96
LZO Decompress rd=39765, wr=65536 @ 0x38dc6e
LZO Decompress rd=22291, wr=65536 @ 0x3977c5
LZO Decompress rd=41569, wr=65536 @ 0x39ceda
LZO Decompress rd=35599, wr=65536 @ 0x3a713d
LZO Decompress rd=23521, wr=65536 @ 0x3afc4e
LZO Decompress rd=27591, wr=65536 @ 0x3b5831
LZO Decompress rd=30727, wr=65536 @ 0x3bc3fa
LZO Decompress rd=37186, wr=65536 @ 0x3c3c03
LZO Decompress rd=31974, wr=65536 @ 0x3ccd47
LZO Decompress rd=31707, wr=65536 @ 0x3d4a2f
LZO Decompress rd=34057, wr=65536 @ 0x3dc60c
LZO Decompress rd=34644, wr=65536 @ 0x3e4b17
LZO Decompress rd=33778, wr=65536 @ 0x3ed26d
LZO Decompress rd=30668, wr=65536 @ 0x3f5661
LZO Decompress rd=28540, wr=65536 @ 0x3fce2f
LZO Decompress rd=30533, wr=65536 @ 0x403dad
LZO Decompress rd=28234, wr=65536 @ 0x40b4f4
LZO Decompress rd=33780, wr=65536 @ 0x412340
LZO Decompress rd=31769, wr=65536 @ 0x41a736
LZO Decompress rd=30934, wr=65536 @ 0x422351
LZO Decompress rd=34476, wr=65536 @ 0x429c29
LZO Decompress rd=27035, wr=65536 @ 0x4322d7
LZO Decompress rd=22689, wr=65536 @ 0x438c74
LZO Decompress rd=31506, wr=65536 @ 0x43e517
LZO Decompress rd=27575, wr=65536 @ 0x44602b
LZO Decompress rd=22224, wr=65536 @ 0x44cbe4
LZO Decompress rd=28652, wr=65536 @ 0x4522b6
LZO Decompress rd=31626, wr=65536 @ 0x4592a4
LZO Decompress rd=26758, wr=65536 @ 0x460e30
LZO Decompress rd=27056, wr=65536 @ 0x4676b8
LZO Decompress rd=29821, wr=65536 @ 0x46e06a
LZO Decompress rd=30168, wr=65536 @ 0x4754e9
LZO Decompress rd=30655, wr=65536 @ 0x47cac3
LZO Decompress rd=29164, wr=65536 @ 0x484284
LZO Decompress rd=28194, wr=65536 @ 0x48b472
LZO Decompress rd=30100, wr=65536 @ 0x492296
LZO Decompress rd=29524, wr=65536 @ 0x49982c
LZO Decompress rd=26909, wr=65536 @ 0x4a0b82
LZO Decompress rd=37295, wr=65536 @ 0x4a74a1
LZO Decompress rd=33080, wr=65536 @ 0x4b0652
LZO Decompress rd=23119, wr=65536 @ 0x4b878c
LZO Decompress rd=27149, wr=65536 @ 0x4be1dd
LZO Decompress rd=30200, wr=65536 @ 0x4c4bec
LZO Decompress rd=26944, wr=65536 @ 0x4cc1e6
LZO Decompress rd=31997, wr=65536 @ 0x4d2b28
LZO Decompress rd=23157, wr=65536 @ 0x4da827
LZO Decompress rd=31523, wr=65536 @ 0x4e029e
LZO Decompress rd=22381, wr=65536 @ 0x4e7dc3
LZO Decompress rd=19553, wr=65536 @ 0x4ed532
LZO Decompress rd=18917, wr=65536 @ 0x4f2195
LZO Decompress rd=18254, wr=65536 @ 0x4f6b7c
LZO Decompress rd=20711, wr=65536 @ 0x4fb2cc
LZO Decompress rd=30840, wr=65536 @ 0x5003b5
LZO Decompress rd=28457, wr=65536 @ 0x507c2f
LZO Decompress rd=23766, wr=65536 @ 0x50eb5a
LZO Decompress rd=22009, wr=65536 @ 0x514832
LZO Decompress rd=31290, wr=65536 @ 0x519e2d
LZO Decompress rd=27216, wr=65536 @ 0x521869
LZO Decompress rd=18883, wr=65536 @ 0x5282bb
LZO Decompress rd=12240, wr=65536 @ 0x52cc80
LZO Decompress rd=16126, wr=65536 @ 0x52fc52
LZO Decompress rd=18562, wr=65536 @ 0x533b52
LZO Decompress rd=23442, wr=65536 @ 0x5383d6
LZO Decompress rd=16788, wr=65536 @ 0x53df6a
LZO Decompress rd=16946, wr=65536 @ 0x542100
LZO Decompress rd=16929, wr=65536 @ 0x546334
LZO Decompress rd=18648, wr=65536 @ 0x54a557
LZO Decompress rd=18865, wr=65536 @ 0x54ee31
LZO Decompress rd=24056, wr=65536 @ 0x5537e4
LZO Decompress rd=22288, wr=65536 @ 0x5595de
LZO Decompress rd=22747, wr=65536 @ 0x55ecf0
LZO Decompress rd=15722, wr=65536 @ 0x5645cd
LZO Decompress rd=16768, wr=65536 @ 0x568339
LZO Decompress rd=27936, wr=65536 @ 0x56c4bb
LZO Decompress rd=1708, wr=65536 @ 0x5731dd
LZO Decompress rd=357, wr=65536 @ 0x57388b
LZO Decompress rd=357, wr=65536 @ 0x5739f2
LZO Decompress rd=357, wr=65536 @ 0x573b59
LZO Decompress rd=15926, wr=65536 @ 0x573cc0
LZO Decompress rd=34152, wr=65536 @ 0x577af8
LZO Decompress rd=31296, wr=65536 @ 0x580062
LZO Decompress rd=32110, wr=65536 @ 0x587aa4
LZO Decompress rd=29832, wr=65536 @ 0x58f814
LZO Decompress rd=8435, wr=65536 @ 0x596c9e
LZO Decompress rd=357, wr=65536 @ 0x598d93
LZO Decompress rd=357, wr=65536 @ 0x598efa
LZO Decompress rd=24189, wr=65536 @ 0x599061
LZO Decompress rd=30175, wr=65536 @ 0x59eee0
LZO Decompress rd=26833, wr=65536 @ 0x5a64c1
LZO Decompress rd=35649, wr=65536 @ 0x5acd94
LZO Decompress rd=33391, wr=65536 @ 0x5b58d7
LZO Decompress rd=31826, wr=65536 @ 0x5bdb48
LZO Decompress rd=32330, wr=65536 @ 0x5c579c
LZO Decompress rd=33139, wr=65536 @ 0x5cd5e8
LZO Decompress rd=38573, wr=65536 @ 0x5d575d
LZO Decompress rd=8824, wr=65536 @ 0x5dee0c
LZO Decompress rd=357, wr=65536 @ 0x5e1086
LZO Decompress rd=357, wr=65536 @ 0x5e11ed
LZO Decompress rd=357, wr=65536 @ 0x5e1354
LZO Decompress rd=357, wr=65536 @ 0x5e14bb
LZO Decompress rd=357, wr=65536 @ 0x5e1622
LZO Decompress rd=2806, wr=65536 @ 0x5e1789
LZO Decompress rd=34333, wr=65536 @ 0x5e2281
LZO Decompress rd=34477, wr=65536 @ 0x5ea8a0
LZO Decompress rd=27736, wr=65536 @ 0x5f2f4f
LZO Decompress rd=35966, wr=65536 @ 0x5f9ba9
LZO Decompress rd=30654, wr=65536 @ 0x602829
LZO Decompress rd=41943, wr=65536 @ 0x609fe9
LZO Decompress rd=45004, wr=65536 @ 0x6143c2
LZO Decompress rd=41191, wr=65536 @ 0x61f390
LZO Decompress rd=41167, wr=65536 @ 0x629479
LZO Decompress rd=44098, wr=65536 @ 0x63354a
LZO Decompress rd=44459, wr=65536 @ 0x63e18e
LZO Decompress rd=44510, wr=65536 @ 0x648f3b
LZO Decompress rd=45324, wr=65536 @ 0x653d1b
LZO Decompress rd=45872, wr=65536 @ 0x65ee29
LZO Decompress rd=45907, wr=65536 @ 0x66a15b
LZO Decompress rd=40148, wr=65536 @ 0x6754b0
LZO Decompress rd=26658, wr=65536 @ 0x67f186
LZO Decompress rd=44351, wr=65536 @ 0x6859aa
LZO Decompress rd=58821, wr=65536 @ 0x6906eb
LZO Decompress rd=42563, wr=65536 @ 0x69ecb2
LZO Decompress rd=36832, wr=65536 @ 0x6a92f7
LZO Decompress rd=42131, wr=65536 @ 0x6b22d9
LZO Decompress rd=49519, wr=65536 @ 0x6bc76e
LZO Decompress rd=54586, wr=65536 @ 0x6c88df
LZO Decompress rd=50216, wr=65536 @ 0x6d5e1b
LZO Decompress rd=48755, wr=65536 @ 0x6e2245
LZO Decompress rd=62504, wr=65536 @ 0x6ee0ba
LZO Decompress rd=61669, wr=61440 @ 0x6fd4e4
LZO Decompress rd=4116, wr=4096 @ 0x70c5cb
LZO Decompress rd=59995, wr=65536 @ 0x70d5e1
LZO Decompress rd=5754, wr=65536 @ 0x71c03e
LZO Decompress rd=3147, wr=65536 @ 0x71d6ba
LZO Decompress rd=3413, wr=13904 @ 0x71e307
Decompressed 5840314 bytes-> 13252176 bytes
usr/share/wave/PDCBeep.wav ... size 3604
etc/layermanager.cfg ... size 109
proc/boot/procnto-instr ... size 413696
usr/bin/pidin ... size 58060
proc/boot/.script ... size 2916
etc/system/config/display_special.conf ... size 424
etc/shells ... size 26
etc/L6Version.txt ... size 10
bin/sloginfo ... size 10011
etc/lbt ... size 1992
etc/system/config/img.conf ... size 243
proc/boot/server.cfg ... size 8
database/dummy ... size 8
proc/boot/libc.so.2 ... size 421888
proc/boot/devc-sersci ... size 62492
etc/inetd.conf ... size 2726
etc/passwd ... size 312
lib/libecpp-ne.so.4 ... size 114688
lib/dll/devg-fpga.so ... size 106496
lib/dll/libGLES_CM.so.1 ... size 130739
proc/boot/pci.cfg ... size 327
lib/dll/img_codec_png.so ... size 140859
usr/share/wave/PDCBeepLoop.wav ... size 1808
etc/profile ... size 595
bin/checkpersistency.sh ... size 82
lib/libsocket.so.2 ... size 139264
usr/lib/libgf.so.1 ... size 103677
usr/share/wave/PDCBeepRearLoop.wav ... size 1808
etc/videoctrl.cfg ... size 1006
usr/lib/libimg.so.1 ... size 72780
usr/share/wave/PDCBeepEnd.wav ... size 946
lib/libasound.so.2 ... size 95805
bin/createHBpersistence.sh ... size 1378
usr/share/wave/PDCBeepRearEnd.wav ... size 942
etc/videowatchdog-L6.cfg ... size 176
lib/libm.so.2 ... size 132543
DSP/DRA300/BootloaderDRA300_rel.bin ... size 928
etc/videoctrlCicMidFake.cfg ... size 891
etc/system/config/display_narrow.conf ... size 423
usr/share/wave/PDCBeepRearStart.wav ... size 352
usr/lib/libffb.so.2 ... size 76862
usr/share/wave/PDCBeepStart.wav ... size 342
etc/hosts ... size 118
etc/shadow ... size 69
etc/ftpusers ... size 67
usr/lib/libmhpfilter.so.1 ... size 12288
lib/dll/deva-ctrl-hb_fpga.so ... size 46694
lib/libcam.so.2 ... size 78078
usr/share/wave/PDCBeepRear.wav ... size 3592
usr/lib/cam-cdrom.so ... size 22441
usr/lib/cam-disk.so ... size 13223
usr/lib/fs-qnx6.so ... size 71923
usr/lib/fs-cd.so ... size 50552
usr/lib/fs-dos.so ... size 81336
usr/lib/fs-udf.so ... size 73690
usr/lib/io-blk.so ... size 158141
lib/dll/dspipc-dra300.so ... size 86016
bin/waitfor ... size 22430
bin/mkdir ... size 10403
bin/cp ... size 35556
bin/slay ... size 17384
bin/sleep ... size 6987
sbin/devf-generic ... size 200104
usr/sbin/tracelogger ... size 18495
usr/bin/on ... size 22430
usr/bin/flashctl ... size 15794
bin/dev-dspipc ... size 81505
bin/fesh ... size 22205
usr/bin/nice ... size 7566
bin/if-test ... size 18662
usr/bin/dev-i2c-hbfpga ... size 40491
usr/bin/memifs2 ... size 45056
usr/bin/slogger ... size 16384
usr/bin/pci-sh7785 ... size 81920
usr/bin/dev-sysregs ... size 65536
sbin/io-display ... size 46132
sbin/io-audio ... size 136336
usr/bin/dev-ipc ... size 69632
usr/bin/dev-videoctrl ... size 49152
usr/bin/dev-mlb ... size 73728
usr/bin/dev-ssi-hbfpga ... size 40960
usr/bin/dev-videowatchdog ... size 40960
usr/bin/dev-spi-hbfpga ... size 69632
usr/bin/vdev-eeprom ... size 139264
usr/bin/vdev-tunnelipc ... size 32768
usr/bin/layermanager ... size 237568
usr/bin/dev-mv2trace ... size 106496
usr/bin/srv-starter-QNX ... size 180224
usr/HBproject/CicMidNavRoot ... size 4857856
bin/infrad ... size 16384
usr/bin/dev-dabatr2740-mid ... size 487424
usr/bin/dev-dabpnp-mid ... size 1036288
bin/ksh ... size 178307
bin/echo ... size 7423
usr/bin/devc-ser8250hb ... size 82833
DSP/DRA300/SHUP_L6_MID_DRI350.bin ... size 1449616
etc/splash_narrow.png ... size 177297
etc/starter.cfg ... size 88096
etc/sysregs-l6-7538.cfg ... size 50943
etc/termcap ... size 6749
etc/config/persistTraceCicMidNavRoot.bin ... size 5926
Image startup_size: 53512 (0xd108)
Image stored_size: 5894240 (0x59f060)
Compressed size: 5840724 (0x591f54)
********** Continue search at: 71f064
********** Process HBCIFS at: 740004
LZO Decompress @0x740044
LZO Decompress rd=33587046, wr=66207872 @ 0x740044
Decompressed 33587046 bytes-> 66207872 bytes
usr/mme/db/mme_connect.sql ... size 856
usr/bin/inetd ... size 45056
sbin/devc-pty ... size 53248
sbin/io-usb ... size 122923
etc/config/umass-enum.cfg ... size 3767
usr/Hmi/otf/socket.cfg ... size 126
usr/bin/cleanEntertainment.sh ... size 109
etc/mme.label ... size 37
usr/bin/vdev-medialaunch ... size 102400
usr/bin/proc_scriptlauncher ... size 16384
usr/bin/dev-nvram ... size 32768
sbin/io-net ... size 77710
etc/post_starting_qdb.sh ... size 102
sbin/pipe ... size 24576
lib/dll/nfm-autoip.so ... size 20531
etc/pre_starting_qdb.sh ... size 3517
usr/bin/createQDBPaths.sh ... size 490
etc/ftpd.conf ... size 36
usr/HBproject/CicMidNavSecond ... size 32727040
usr/bin/vdev-flexgps ... size 278528
usr/bin/ndr ... size 593920
usr/bin/vdev-logvolmgr ... size 241664
usr/bin/usbPowerMonitor ... size 32768
usr/bin/multicored ... size 217088
usr/bin/srv_drivehandler ... size 335872
sbin/mcd ... size 45056
usr/sbin/io-media-margi ... size 270336
usr/sbin/srv-mmelauncher ... size 45056
usr/bin/dev-adjmanager ... size 40960
usr/bin/devb-sdc-hbfpga ... size 118784
usr/bin/devb-eide-hbfpga ... size 121751
usr/lib/terminfo/q/qvt101 ... size 1048
usr/Hmi/otf/start_otf.sh ... size 68
usr/Hmi/otf/BMWOTFagent ... size 32768
usr/Hmi/otf/libBMWOTFapi.so.1 ... size 32768
usr/Hmi/otf/libBMWOTFapi.so.2 ... size 28672
usr/Hmi/otf/libBMWOTFapi.so.3 ... size 28672
usr/Hmi/otf/libBMWOTFdrvMCD.so.1 ... size 16384
usr/Hmi/otf/libBMWOTFdrvSerial.so.1 ... size 20480
usr/Hmi/otf/libBMWOTFdrvSocket.so.1 ... size 12288
usr/Hmi/bin/HmiMain ... size 16764928
usr/bin/dumper ... size 24103
usr/bin/HUShutdown.sh ... size 406
usr/sbin/sqlite_console ... size 48641
etc/fstab ... size 353
usr/sbin/mme ... size 1261569
etc/ipod.cfg ... size 3441
usr/bin/runPidin.sh ... size 639
usr/sbin/qdb ... size 128425
etc/mmelauncher.cfg ... size 2597
bin/flashit ... size 13707
usr/bin/netinit.sh ... size 2457
lib/dll/devu-ehci.so ... size 36253
etc/ipf.conf ... size 553
lib/dll/devu-ohci.so ... size 29545
etc/mcd.conf ... size 2953
lib/dll/devn-asix.so ... size 73046
bin/sercd.sh ... size 288
bin/mount ... size 15965
bin/umount ... size 6707
usr/lib/terminfo/q/qnx2 ... size 1460
bin/ls ... size 20075
bin/ln ... size 11472
etc/dotMmeDotDelete.sh ... size 813
opt/bin/fs-cifs ... size 87441
usr/lib/terminfo/v/vs100 ... size 2384
bin/login ... size 20657
usr/bin/runDumper.sh ... size 2894
etc/mmelauncher_upgrade_mme_custom_4.sh ... size 1025
usr/bin/rm ... size 10380
etc/mmelauncher_upgrade_mme_29.sh ... size 1862
bin/gzip ... size 58262
usr/mme/db/qdb.cfg ... size 2758
usr/sbin/telnetd ... size 125940
usr/lib/terminfo/v/vi200-f ... size 1035
usr/sbin/ftpd ... size 94542
usr/lib/terminfo/x/xterm ... size 2384
usr/lib/terminfo/q/qnxt2 ... size 1371
usr/sbin/if_up ... size 7981
usr/lib/libexpat.so.2 ... size 77072
usr/sbin/pppd ... size 185568
usr/lib/terminfo/q/qansi-m ... size 2357
sbin/sysctl ... size 19604
etc/mmelauncher_upgrade_mme_28.sh ... size 845
sbin/route ... size 29410
usr/lib/terminfo/q/qansi-w ... size 2357
usr/lib/terminfo/v/viewpoint ... size 972
lib/dll/npm-tcpip-v4.so ... size 355185
usr/lib/terminfo/q/qvt108 ... size 1048
lib/dll/npm-pppmgr.so ... size 94082
usr/lib/libsac.so ... size 8192
usr/lib/libpal_core.so ... size 57344
usr/lib/libparsercreator.so ... size 32768
usr/lib/libpdiparser.so ... size 118784
lib/dll/lsm-ipfilter-v4.so ... size 98304
usr/sbin/ipf ... size 39049
usr/lib/terminfo/q/qnxm ... size 1758
usr/sbin/ipnat ... size 33486
usr/lib/terminfo/q/qansi-t ... size 2301
usr/lib/terminfo/v/visual ... size 1035
usr/bin/vdev-fsys-dbc ... size 29502
usr/lib/terminfo/q/qansi ... size 2295
etc/mmelauncher_upgrade_mme_library_0.sh ... size 956
usr/sbin/io-fs ... size 139264
usr/bin/tar ... size 320497
usr/lib/terminfo/x/xterm-q ... size 2294
usr/bin/fdisk ... size 101640
usr/bin/mkqnx6fs ... size 83342
usr/lib/terminfo/q/qansi-g ... size 2092
usr/bin/chattr ... size 9627
usr/lib/terminfo/v/vt102-plus ... size 1987
lib/dll/devn-micrel8841.so ... size 58018
usr/lib/terminfo/t/test ... size 1984
etc/mmelauncher_upgrade_mme_custom_3.sh ... size 1398
usr/bin/dhcp.client ... size 64676
etc/mmelauncher_upgrade_mme_library_8.sh ... size 798
sbin/ifconfig ... size 37411
usr/lib/terminfo/x/xterm-m ... size 1930
etc/mmelauncher_upgrade_mme_custom_27.sh ... size 1598
sbin/devb-umass ... size 30716
etc/config/default_scopes_drivehandler.hbtc ... size 1916
sbin/chkqnx6fs ... size 32442
sbin/chkfsys ... size 38008
usr/lib/terminfo/v/vs100s ... size 1913
etc/mmelauncher_upgrade_mme_custom_16.sh ... size 1034
usr/bin/touch ... size 9190
usr/lib/terminfo/x/xterms ... size 1913
usr/lib/terminfo/a/ansi ... size 1179
bin/sync ... size 6037
usr/lib/terminfo/q/qnxw ... size 1748
usr/lib/libproject_qnxapp_collect_srvlayermanager_client.so ... size 24576
lib/libusbdi.so.2 ... size 48079
etc/mmelauncher_upgrade_mme_custom_17.sh ... size 1034
lib/dll/libfont.so.1 ... size 53248
usr/lib/libFF-T2K-cache.so.2 ... size 9693
usr/lib/terminfo/q/qnxtmono ... size 1707
usr/lib/libFF-T2K-fm.so.1 ... size 14087
usr/lib/terminfo/v/vt102 ... size 1703
usr/lib/libFF-T2K.so.2 ... size 262775
usr/lib/terminfo/v/vt102-am ... size 1703
usr/lib/terminfo/q/qnxt ... size 1686
usr/lib/libz.so.2 ... size 69915
usr/lib/terminfo/q/qnxt4 ... size 1686
usr/mme/db/mme_custom.sql ... size 1661
lib/dll/libhiddi.so.1 ... size 40960
usr/lib/libpal_audio.so ... size 20480
usr/lib/libpal_bt.so ... size 28672
usr/lib/libscp_core.so ... size 176128
usr/lib/libsse.so ... size 278528
usr/lib/libsvox.so ... size 741376
usr/lib/libtools.so ... size 626688
usr/lib/libaliveservice.so ... size 16384
usr/lib/libaudiocoder.so ... size 16384
usr/lib/libaudiocoder_ans.so ... size 20480
usr/lib/libaudiocoder_tts.so ... size 61440
usr/lib/libaudiomatrixservice.so ... size 81920
usr/lib/libdsr.so ... size 405504
usr/lib/libhostagent.so ... size 20480
usr/lib/libmonitorservice.so ... size 73728
usr/lib/libprompterservice.so ... size 225280
usr/lib/librecognitionservice.so ... size 266240
usr/lib/librmssservice.so ... size 40960
usr/lib/libsaipservice.so ... size 90112
usr/lib/libsaopservice.so ... size 53248
usr/lib/libscfservice.so ... size 90112
usr/lib/libspellmatcherservice.so ... size 229376
usr/lib/libsss_config.so ... size 8192
usr/lib/libtnservice.so ... size 151552
usr/lib/libunidb_sqlite3so.so ... size 24576
usr/lib/libhbsystime_posix_1_0.so ... size 8192
lib/libdspipc.so ... size 24576
usr/lib/libmldr.so ... size 49152
usr/lib/libsqlite3.so.1 ... size 471040
usr/lib/libthirdparty_qdb_icu_3_5_bmw.so ... size 24576
usr/lib/libthirdparty_icu_3_5_bmw.so ... size 1191936
usr/lib/libasiacollation.so ... size 53248
usr/bin/qdblauncher ... size 18428
usr/lib/terminfo/q/qnx ... size 1491
usr/lib/libmmfilter.so.1 ... size 16384
usr/lib/libmmedia.so.1 ... size 45056
usr/lib/libaoi.so.1 ... size 16384
usr/lib/libmme.so.1 ... size 45056
usr/lib/libqdb.so.1 ... size 32768
usr/lib/libxml2.so.1 ... size 602112
lib/dll/mmedia/aac_parser.so ... size 57344
lib/dll/mmedia/cdda_parser.so ... size 20480
lib/dll/mmedia/cdda_streamer.so ... size 20480
lib/dll/mmedia/fildes_streamer.so ... size 16384
lib/dll/mmedia/media_streamer.so ... size 20480
lib/dll/mmedia/mmipc_writer.so ... size 61440
lib/dll/mmedia/mpega_parser.so ... size 61440
lib/dll/mmedia/mp4_parser.so ... size 94208
lib/dll/mmedia/queue_filter.so ... size 16384
lib/dll/mmedia/stream_reader.so ... size 20480
lib/dll/mmedia/wma9_parser.so ... size 274432
usr/bin/scp ... size 40960
usr/bin/devb-sercd-hbfpga ... size 100867
usr/bin/icudt35l.dat ... size 892560
etc/mmelauncher_upgrade_mme_22.sh ... size 36366
etc/mmelauncher_upgrade_mme_library_6.sh ... size 34435
etc/config/persistTraceCicMidNavSecond.bin ... size 33217
etc/sss/ar_XA/default.cfg ... size 33165
etc/sss/de_DE/default.cfg ... size 33165
etc/sss/el_GR/default.cfg ... size 33165
etc/sss/en_GB/default.cfg ... size 33165
etc/sss/en_US/default.cfg ... size 33165
etc/sss/fr_FR/default.cfg ... size 33165
etc/sss/es_ES/default.cfg ... size 33165
etc/sss/hu_HU/default.cfg ... size 33165
etc/sss/it_IT/default.cfg ... size 33165
etc/sss/nl_NL/default.cfg ... size 33165
etc/sss/pl_PL/default.cfg ... size 33165
etc/sss/pt_PT/default.cfg ... size 33165
etc/sss/ru_RU/default.cfg ... size 33165
etc/sss/sv_SE/default.cfg ... size 33165
etc/sss/tr_TR/default.cfg ... size 33165
etc/sss/en_RR/default.cfg ... size 32851
usr/mme/db/mme.sql ... size 32134
etc/mme.conf.CD ... size 20631
etc/mme.conf.DVD ... size 20471
usr/mme/db/mme_library.sql ... size 12084
usr/bin/mnt_hd.sh ... size 8214
etc/mmelauncher_upgrade_mme_custom_26.sh ... size 6784
usr/mme/db/mme_mp3_speech.sql ... size 6540
etc/io-media-margi.cfg ... size 6214
usr/mme/db/mme_data.sql ... size 5658
usr/mme/db/mme_temp.sql ... size 4337
usr/lib/terminfo/q/qnx4 ... size 1491
usr/lib/terminfo/q/qnxs2 ... size 1460
usr/lib/terminfo/v/vt100 ... size 1388
usr/lib/terminfo/v/vt100-am ... size 1388
etc/mmelauncher_upgrade_mme_custom_2.sh ... size 1385
etc/ipnat.conf ... size 1293
etc/mmelauncher_upgrade_mme_10.sh ... size 1241
etc/mmelauncher_upgrade_mme_11.sh ... size 1241
etc/mmelauncher_upgrade_mme_12.sh ... size 1241
etc/mmelauncher_upgrade_mme_13.sh ... size 1241
etc/mmelauncher_upgrade_mme_14.sh ... size 1241
etc/mmelauncher_upgrade_mme_15.sh ... size 1241
etc/mmelauncher_upgrade_mme_16.sh ... size 1241
etc/mmelauncher_upgrade_mme_17.sh ... size 1241
etc/mmelauncher_upgrade_mme_18.sh ... size 1241
etc/mmelauncher_upgrade_mme_19.sh ... size 1241
etc/mmelauncher_upgrade_mme_20.sh ... size 1241
etc/mmelauncher_upgrade_mme_21.sh ... size 1241
etc/mmelauncher_upgrade_mme_23.sh ... size 1241
etc/mmelauncher_upgrade_mme_24.sh ... size 1241
etc/mmelauncher_upgrade_mme_25.sh ... size 1241
etc/mmelauncher_upgrade_mme_26.sh ... size 1241
etc/mmelauncher_upgrade_mme_27.sh ... size 1241
etc/mmelauncher_upgrade_mme_0.sh ... size 1238
etc/mmelauncher_upgrade_mme_1.sh ... size 1238
etc/mmelauncher_upgrade_mme_2.sh ... size 1238
etc/mmelauncher_upgrade_mme_3.sh ... size 1238
etc/mmelauncher_upgrade_mme_4.sh ... size 1238
etc/mmelauncher_upgrade_mme_5.sh ... size 1238
etc/mmelauncher_upgrade_mme_6.sh ... size 1238
etc/mmelauncher_upgrade_mme_7.sh ... size 1238
etc/mmelauncher_upgrade_mme_8.sh ... size 1238
etc/mmelauncher_upgrade_mme_9.sh ... size 1238
usr/lib/terminfo/q/qvt102 ... size 1033
etc/mmelauncher_upgrade_mme_custom_10.sh ... size 1030
etc/mmelauncher_upgrade_mme_custom_11.sh ... size 1030
etc/mmelauncher_upgrade_mme_custom_12.sh ... size 1030
etc/mmelauncher_upgrade_mme_custom_13.sh ... size 1030
etc/mmelauncher_upgrade_mme_custom_14.sh ... size 1030
etc/mmelauncher_upgrade_mme_custom_15.sh ... size 1030
etc/mmelauncher_upgrade_mme_custom_19.sh ... size 1030
etc/mmelauncher_upgrade_mme_custom_20.sh ... size 1030
etc/mmelauncher_upgrade_mme_custom_21.sh ... size 1030
etc/mmelauncher_upgrade_mme_custom_22.sh ... size 1030
etc/mmelauncher_upgrade_mme_custom_23.sh ... size 1030
etc/mmelauncher_upgrade_mme_custom_24.sh ... size 1030
etc/mmelauncher_upgrade_mme_custom_25.sh ... size 1030
etc/mmelauncher_upgrade_mme_custom_18.sh ... size 1027
etc/mmelauncher_upgrade_mme_custom_5.sh ... size 1025
etc/mmelauncher_upgrade_mme_custom_6.sh ... size 1025
etc/mmelauncher_upgrade_mme_custom_7.sh ... size 1025
etc/mmelauncher_upgrade_mme_custom_8.sh ... size 1025
etc/mmelauncher_upgrade_mme_custom_9.sh ... size 1025
etc/hfs.cfg ... size 1006
etc/mmelauncher_upgrade_mme_library_1.sh ... size 956
etc/mmelauncher_upgrade_mme_library_2.sh ... size 956
etc/mmelauncher_upgrade_mme_library_3.sh ... size 956
etc/mmelauncher_upgrade_mme_library_4.sh ... size 956
etc/mmelauncher_upgrade_mme_library_5.sh ... size 956
etc/mmelauncher_upgrade_mme_library_7.sh ... size 956
etc/mmelauncher_upgrade_mme_custom_0.sh ... size 950
etc/mmelauncher_upgrade_mme_custom_1.sh ... size 950
usr/lib/terminfo/v/vt52 ... size 905
********** Continue search at: 2747faa
Nothing left to extract from 9283251A.0pb
CicMidNavSecond Disassembly
9. Disassemble “CicMidNavSecond” with Ghidra. This is a 30+ MB binary, and takes a really long time to fully process.
10. Using the same process as the CIC Premium/High, looking for common byte strings used in encryption routines, the same MD5 init seed “0x67452301” was found.
11. The same “.swt” key files were identified as strings in the CIC, the same “1B” file and file header is used, and even more surprisingly the same RSA E and modulo keys appear to be used.
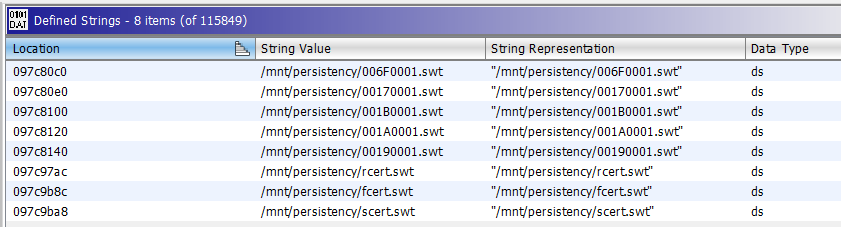
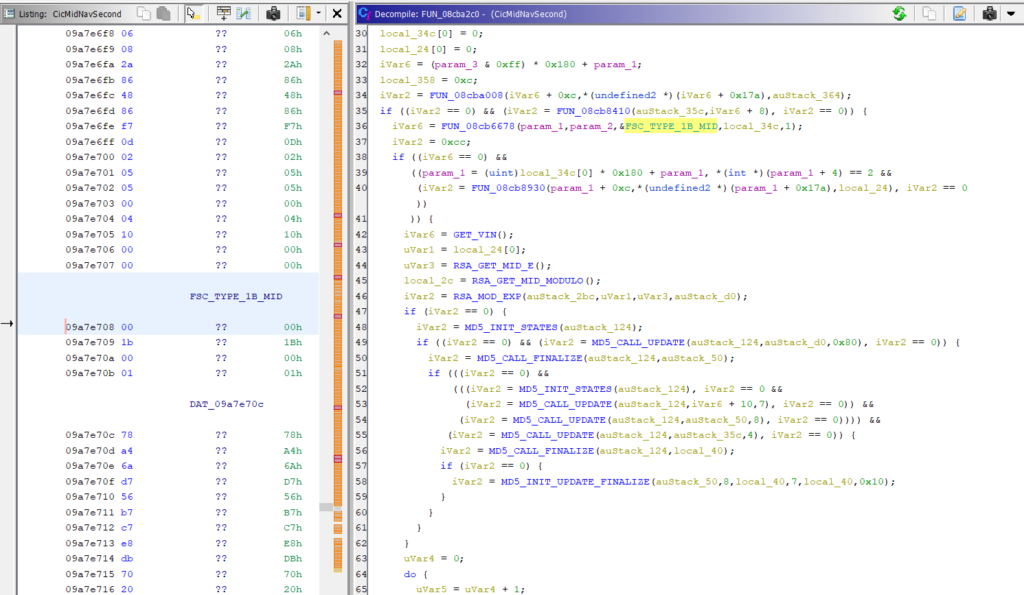
12. Comparing the Main Key routines, both algorithms appear identical, using the same RSA ModExp, MD5 and DES rounds as the CIC High.
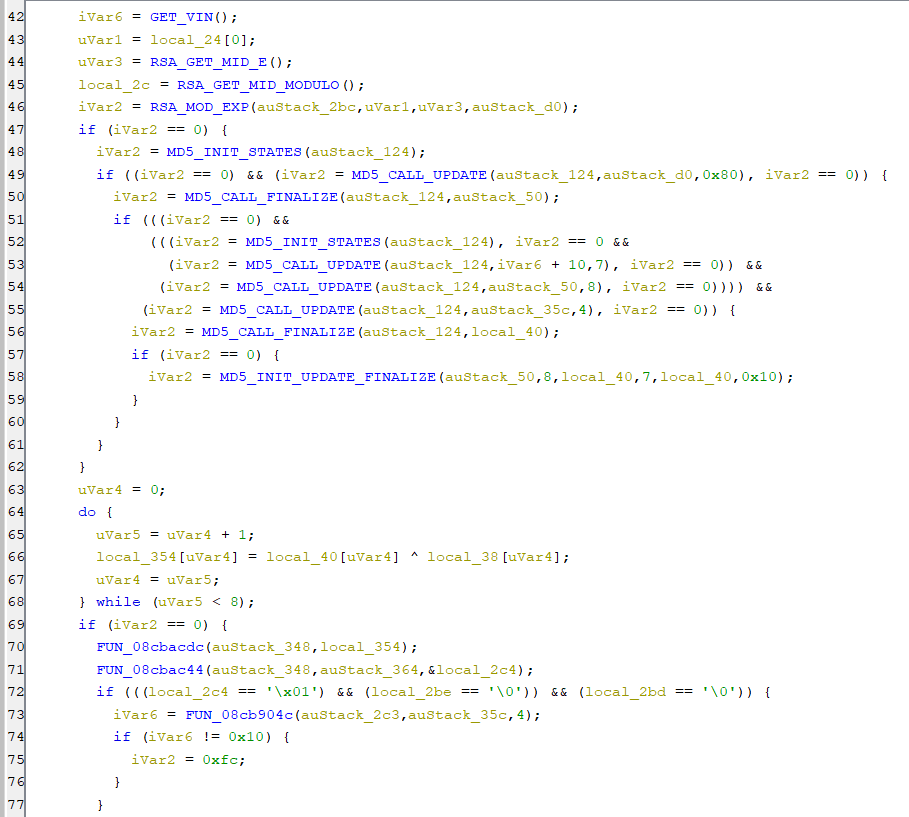
13. Without a CIC Mid to test, it appears that the same keygen could be used to generate the map activation code as the CIC High.
Title picture borrowed from : https://mca.electricmura.ro/en/blog-bmw-mask-ccc-cic-or-nbt-idrive/
