The BMW CIC is the Premium headunit from ~2009 – 2013, and included navigation stored on an internal hard drive. BMW released annual map updates for the CIC until ~2021, however these maps were not free of charge. Any attempt to install the map through the USB glovebox results in a request for a 20-character activation code. Although free key generators are available online, I thought it would be interesting to see if I could make an activation code and create a keygen by reverse engineering the firmware.
CIC (Premium) Keygen Source Code
Since there are a number of available keygens already, the source code for the key generation routine is available here: https://www.reverseeng.dev/Files/CIC/create_cic_fsc.7z
Dump the Firmware
1. Download the E89 spDaten pack intended for Rheingold updates, and extract 9283426A.0pb from the data\CI63F1 folder. I assumed the “CI” folder set was for the “CIC”, and this file was chosen as the “9283….0pb” files were the largest in the folder, and “…426A” was the highest revision of the “9283…” series.
2. Unpacking the 9283426A.0pb file.
QNX uses IFS files to store firmware. Conveniently, QNX dumpifs source code was available here: https://github.com/askac/dumpifs However, when used “/full/path/to/dumpifs/dumpIfs.sh 9283426A.0pb 9283426A_dump” it only dumped part of the firmware, and did not appear to contain the elf needed for CICHigh.
./dumpIfs.sh 9283426A.0pb 9283426A/
Image startup_size: 53512 (0xd108)
Image stored_size: 4831360 (0x49b880)
Compressed size: 4777844 (0x48e774)
LZO Decompress @0xcd10c
nowPtr cd10c c1 85 c2 8f len 858f
lzo1x_decompress(buf, 1407945374...)
LZO Decompress rd=34191, wr=65536 @ 0xcd10c
nowPtr d569d c1 90 c2 e1 len 90e1
lzo1x_decompress(buf, 1407945615...)
LZO Decompress rd=37089, wr=65536 @ 0xd569d
nowPtr de780 c1 9a c2 13 len 9a13
lzo1x_decompress(buf, 1407944210...)
LZO Decompress rd=39443, wr=65536 @ 0xde780
nowPtr e8195 c1 97 c2 1c len 971c
lzo1x_decompress(buf, 1407945991...)
LZO Decompress rd=38684, wr=65536 @ 0xe8195
nowPtr f18b3 c1 86 c2 ed len 86ed
lzo1x_decompress(buf, 1407947781...)
LZO Decompress rd=34541, wr=65536 @ 0xf18b3
nowPtr f9fa2 c1 9b c2 32 len 9b32
lzo1x_decompress(buf, 1407943764...)
LZO Decompress rd=39730, wr=65536 @ 0xf9fa2
nowPtr 103ad6 c1 52 c2 47 len 5247
lzo1x_decompress(buf, 1407947144...)
LZO Decompress rd=21063, wr=65536 @ 0x103ad6
nowPtr 108d1f c1 67 c2 ab len 67ab
lzo1x_decompress(buf, 1407944977...)
LZO Decompress rd=26539, wr=65536 @ 0x108d1f
nowPtr 10f4cc c1 73 c2 d6 len 73d6
lzo1x_decompress(buf, 1407946014...)
LZO Decompress rd=29654, wr=65536 @ 0x10f4cc
nowPtr 1168a4 c1 88 c2 32 len 8832
lzo1x_decompress(buf, 1407943808...)
LZO Decompress rd=34866, wr=65536 @ 0x1168a4
nowPtr 11f0d8 c1 90 c2 ff len 90ff
lzo1x_decompress(buf, 1407944202...)
LZO Decompress rd=37119, wr=65536 @ 0x11f0d8
nowPtr 1281d9 c1 96 c2 df len 96df
lzo1x_decompress(buf, 1407945995...)
LZO Decompress rd=38623, wr=65536 @ 0x1281d9
nowPtr 1318ba c1 96 c2 24 len 9624
lzo1x_decompress(buf, 1407947532...)
LZO Decompress rd=38436, wr=65536 @ 0x1318ba
nowPtr 13aee0 c1 78 c2 fd len 78fd
lzo1x_decompress(buf, 1407943762...)
LZO Decompress rd=30973, wr=65536 @ 0x13aee0
nowPtr 1427df c1 82 c2 7a len 827a
lzo1x_decompress(buf, 1407946385...)
LZO Decompress rd=33402, wr=65536 @ 0x1427df
nowPtr 14aa5b c1 71 c2 96 len 7196
lzo1x_decompress(buf, 1407946765...)
LZO Decompress rd=29078, wr=65536 @ 0x14aa5b
nowPtr 151bf3 c1 61 c2 b0 len 61b0
lzo1x_decompress(buf, 1407947269...)
LZO Decompress rd=25008, wr=65536 @ 0x151bf3
nowPtr 157da5 c1 8b c2 1e len 8b1e
lzo1x_decompress(buf, 1407946007...)
LZO Decompress rd=35614, wr=65536 @ 0x157da5
nowPtr 1608c5 c1 83 c2 fb len 83fb
lzo1x_decompress(buf, 1407947031...)
LZO Decompress rd=33787, wr=65536 @ 0x1608c5
nowPtr 168cc2 c1 6c c2 f6 len 6cf6
lzo1x_decompress(buf, 1407946260...)
LZO Decompress rd=27894, wr=65536 @ 0x168cc2
nowPtr 16f9ba c1 7b c2 34 len 7b34
lzo1x_decompress(buf, 1407944972...)
LZO Decompress rd=31540, wr=65536 @ 0x16f9ba
nowPtr 1774f0 c1 85 c2 30 len 8530
lzo1x_decompress(buf, 1407946370...)
LZO Decompress rd=34096, wr=65536 @ 0x1774f0
nowPtr 17fa22 c1 87 c2 31 len 8731
lzo1x_decompress(buf, 1407944084...)
LZO Decompress rd=34609, wr=65536 @ 0x17fa22
nowPtr 188155 c1 88 c2 b4 len 88b4
lzo1x_decompress(buf, 1407946375...)
LZO Decompress rd=34996, wr=65536 @ 0x188155
nowPtr 190a0b c1 90 c2 4c len 904c
lzo1x_decompress(buf, 1407946397...)
LZO Decompress rd=36940, wr=65536 @ 0x190a0b
nowPtr 199a59 c1 77 c2 8b len 778b
lzo1x_decompress(buf, 1407944203...)
LZO Decompress rd=30603, wr=65536 @ 0x199a59
nowPtr 1a11e6 c1 86 c2 d5 len 86d5
lzo1x_decompress(buf, 1407946008...)
LZO Decompress rd=34517, wr=65536 @ 0x1a11e6
nowPtr 1a98bd c1 6a c2 1 len 6a01
lzo1x_decompress(buf, 1407944463...)
LZO Decompress rd=27137, wr=65536 @ 0x1a98bd
nowPtr 1b02c0 c1 6e c2 80 len 6e80
lzo1x_decompress(buf, 1407944082...)
LZO Decompress rd=28288, wr=65536 @ 0x1b02c0
nowPtr 1b7142 c1 6d c2 9e len 6d9e
lzo1x_decompress(buf, 1407947540...)
LZO Decompress rd=28062, wr=65536 @ 0x1b7142
nowPtr 1bdee2 c1 5e c2 74 len 5e74
lzo1x_decompress(buf, 1407943764...)
LZO Decompress rd=24180, wr=65536 @ 0x1bdee2
nowPtr 1c3d58 c1 58 c2 e3 len 58e3
lzo1x_decompress(buf, 1407945354...)
LZO Decompress rd=22755, wr=65536 @ 0x1c3d58
nowPtr 1c963d c1 7c c2 65 len 7c65
lzo1x_decompress(buf, 1407944463...)
LZO Decompress rd=31845, wr=65536 @ 0x1c963d
nowPtr 1d12a4 c1 63 c2 f9 len 63f9
lzo1x_decompress(buf, 1407945494...)
LZO Decompress rd=25593, wr=65536 @ 0x1d12a4
nowPtr 1d769f c1 70 c2 78 len 7078
lzo1x_decompress(buf, 1407945617...)
LZO Decompress rd=28792, wr=65536 @ 0x1d769f
nowPtr 1de719 c1 64 c2 69 len 6469
lzo1x_decompress(buf, 1407946635...)
LZO Decompress rd=25705, wr=65536 @ 0x1de719
nowPtr 1e4b84 c1 7c c2 c0 len 7cc0
lzo1x_decompress(buf, 1407945878...)
LZO Decompress rd=31936, wr=65536 @ 0x1e4b84
nowPtr 1ec846 c1 8f c2 4f len 8f4f
lzo1x_decompress(buf, 1407945624...)
LZO Decompress rd=36687, wr=65536 @ 0x1ec846
nowPtr 1f5797 c1 75 c2 bf len 75bf
lzo1x_decompress(buf, 1407947145...)
LZO Decompress rd=30143, wr=65536 @ 0x1f5797
nowPtr 1fcd58 c1 8c c2 15 len 8c15
lzo1x_decompress(buf, 1407946122...)
LZO Decompress rd=35861, wr=65536 @ 0x1fcd58
nowPtr 20596f c1 7f c2 32 len 7f32
lzo1x_decompress(buf, 1407945985...)
LZO Decompress rd=32562, wr=65536 @ 0x20596f
nowPtr 20d8a3 c1 84 c2 95 len 8495
lzo1x_decompress(buf, 1407947157...)
LZO Decompress rd=33941, wr=65536 @ 0x20d8a3
nowPtr 215d3a c1 8e c2 17 len 8e17
lzo1x_decompress(buf, 1407946636...)
LZO Decompress rd=36375, wr=65536 @ 0x215d3a
nowPtr 21eb53 c1 78 c2 44 len 7844
lzo1x_decompress(buf, 1407944709...)
LZO Decompress rd=30788, wr=65536 @ 0x21eb53
nowPtr 226399 c1 7a c2 dc len 7adc
lzo1x_decompress(buf, 1407947403...)
LZO Decompress rd=31452, wr=65536 @ 0x226399
nowPtr 22de77 c1 5e c2 7a len 5e7a
lzo1x_decompress(buf, 1407947017...)
LZO Decompress rd=24186, wr=65536 @ 0x22de77
nowPtr 233cf3 c1 6a c2 d5 len 6ad5
lzo1x_decompress(buf, 1407945733...)
LZO Decompress rd=27349, wr=65536 @ 0x233cf3
nowPtr 23a7ca c1 87 c2 61 len 8761
lzo1x_decompress(buf, 1407947676...)
LZO Decompress rd=34657, wr=65536 @ 0x23a7ca
nowPtr 242f2d c1 7e c2 dc len 7edc
lzo1x_decompress(buf, 1407943807...)
LZO Decompress rd=32476, wr=65536 @ 0x242f2d
nowPtr 24ae0b c1 5c c2 dd len 5cdd
lzo1x_decompress(buf, 1407946525...)
LZO Decompress rd=23773, wr=65536 @ 0x24ae0b
nowPtr 250aea c1 5f c2 ea len 5fea
lzo1x_decompress(buf, 1407946524...)
LZO Decompress rd=24554, wr=65536 @ 0x250aea
nowPtr 256ad6 c1 7d c2 d6 len 7dd6
lzo1x_decompress(buf, 1407945992...)
LZO Decompress rd=32214, wr=65536 @ 0x256ad6
nowPtr 25e8ae c1 59 c2 2a len 592a
lzo1x_decompress(buf, 1407944224...)
LZO Decompress rd=22826, wr=65536 @ 0x25e8ae
nowPtr 2641da c1 67 c2 c9 len 67c9
lzo1x_decompress(buf, 1407946252...)
LZO Decompress rd=26569, wr=65536 @ 0x2641da
nowPtr 26a9a5 c1 8e c2 ac len 8eac
lzo1x_decompress(buf, 1407945879...)
LZO Decompress rd=36524, wr=65536 @ 0x26a9a5
nowPtr 273853 c1 76 c2 a3 len 76a3
lzo1x_decompress(buf, 1407947525...)
LZO Decompress rd=30371, wr=65536 @ 0x273853
nowPtr 27aef8 c1 75 c2 50 len 7550
lzo1x_decompress(buf, 1407943722...)
LZO Decompress rd=30032, wr=65536 @ 0x27aef8
nowPtr 28244a c1 7b c2 a5 len 7ba5
lzo1x_decompress(buf, 1407947804...)
LZO Decompress rd=31653, wr=65536 @ 0x28244a
nowPtr 289ff1 c1 79 c2 4d len 794d
lzo1x_decompress(buf, 1407946115...)
LZO Decompress rd=31053, wr=65536 @ 0x289ff1
nowPtr 291940 c1 68 c2 f4 len 68f4
lzo1x_decompress(buf, 1407944338...)
LZO Decompress rd=26868, wr=65536 @ 0x291940
nowPtr 298236 c1 68 c2 42 len 6842
lzo1x_decompress(buf, 1407946376...)
LZO Decompress rd=26690, wr=65536 @ 0x298236
nowPtr 29ea7a c1 72 c2 45 len 7245
lzo1x_decompress(buf, 1407947020...)
LZO Decompress rd=29253, wr=65536 @ 0x29ea7a
nowPtr 2a5cc1 c1 7c c2 48 len 7c48
lzo1x_decompress(buf, 1407946003...)
LZO Decompress rd=31816, wr=65536 @ 0x2a5cc1
nowPtr 2ad90b c1 77 c2 12 len 7712
lzo1x_decompress(buf, 1407943808...)
LZO Decompress rd=30482, wr=65536 @ 0x2ad90b
nowPtr 2b501f c1 73 c2 92 len 7392
lzo1x_decompress(buf, 1407944721...)
LZO Decompress rd=29586, wr=65536 @ 0x2b501f
nowPtr 2bc3b3 c1 75 c2 e8 len 75e8
lzo1x_decompress(buf, 1407946245...)
LZO Decompress rd=30184, wr=65536 @ 0x2bc3b3
nowPtr 2c399d c1 5e c2 fd len 5efd
lzo1x_decompress(buf, 1407945999...)
LZO Decompress rd=24317, wr=65536 @ 0x2c399d
nowPtr 2c989c c1 1f c2 1b len 1f1b
lzo1x_decompress(buf, 1407945742...)
LZO Decompress rd=7963, wr=65536 @ 0x2c989c
nowPtr 2cb7b9 c1 59 c2 eb len 59eb
lzo1x_decompress(buf, 1407944203...)
LZO Decompress rd=23019, wr=65536 @ 0x2cb7b9
nowPtr 2d11a6 c1 82 c2 4b len 824b
lzo1x_decompress(buf, 1407944728...)
LZO Decompress rd=33355, wr=65536 @ 0x2d11a6
nowPtr 2d93f3 c1 7f c2 67 len 7f67
lzo1x_decompress(buf, 1407944581...)
LZO Decompress rd=32615, wr=65536 @ 0x2d93f3
nowPtr 2e135c c1 37 c2 48 len 3748
lzo1x_decompress(buf, 1407946510...)
LZO Decompress rd=14152, wr=65536 @ 0x2e135c
nowPtr 2e4aa6 c1 67 c2 ef len 67ef
lzo1x_decompress(buf, 1407944344...)
LZO Decompress rd=26607, wr=65536 @ 0x2e4aa6
nowPtr 2eb297 c1 56 c2 4 len 5604
lzo1x_decompress(buf, 1407945993...)
LZO Decompress rd=22020, wr=65536 @ 0x2eb297
nowPtr 2f089d c1 a1 c2 73 len a173
lzo1x_decompress(buf, 1407946383...)
LZO Decompress rd=41331, wr=65536 @ 0x2f089d
nowPtr 2faa12 c1 a4 c2 4 len a404
lzo1x_decompress(buf, 1407947396...)
LZO Decompress rd=41988, wr=65536 @ 0x2faa12
nowPtr 304e18 c1 59 c2 7c len 597c
lzo1x_decompress(buf, 1407945738...)
LZO Decompress rd=22908, wr=65536 @ 0x304e18
nowPtr 30a796 c1 67 c2 48 len 6748
lzo1x_decompress(buf, 1407947528...)
LZO Decompress rd=26440, wr=65536 @ 0x30a796
nowPtr 310ee0 c1 78 c2 e2 len 78e2
lzo1x_decompress(buf, 1407943730...)
LZO Decompress rd=30946, wr=65536 @ 0x310ee0
nowPtr 3187c4 c1 86 c2 1b len 861b
lzo1x_decompress(buf, 1407947286...)
LZO Decompress rd=34331, wr=65536 @ 0x3187c4
nowPtr 320de1 c1 7c c2 7e len 7c7e
lzo1x_decompress(buf, 1407946387...)
LZO Decompress rd=31870, wr=65536 @ 0x320de1
nowPtr 328a61 c1 82 c2 d8 len 82d8
lzo1x_decompress(buf, 1407947155...)
LZO Decompress rd=33496, wr=65536 @ 0x328a61
nowPtr 330d3b c1 7a c2 55 len 7a55
lzo1x_decompress(buf, 1407945741...)
LZO Decompress rd=31317, wr=65536 @ 0x330d3b
nowPtr 338792 c1 98 c2 9 len 9809
lzo1x_decompress(buf, 1407947780...)
LZO Decompress rd=38921, wr=65536 @ 0x338792
nowPtr 341f9d c1 7c c2 41 len 7c41
lzo1x_decompress(buf, 1407943759...)
LZO Decompress rd=31809, wr=65536 @ 0x341f9d
nowPtr 349be0 c1 77 c2 34 len 7734
lzo1x_decompress(buf, 1407944594...)
LZO Decompress rd=30516, wr=65536 @ 0x349be0
nowPtr 351316 c1 73 c2 33 len 7333
lzo1x_decompress(buf, 1407945352...)
LZO Decompress rd=29491, wr=65536 @ 0x351316
nowPtr 35864b c1 76 c2 b7 len 76b7
lzo1x_decompress(buf, 1407947037...)
LZO Decompress rd=30391, wr=65536 @ 0x35864b
nowPtr 35fd04 c1 75 c2 65 len 7565
lzo1x_decompress(buf, 1407944342...)
LZO Decompress rd=30053, wr=65536 @ 0x35fd04
nowPtr 36726b c1 93 c2 6b len 936b
lzo1x_decompress(buf, 1407945245...)
LZO Decompress rd=37739, wr=65536 @ 0x36726b
nowPtr 3705d8 c1 68 c2 48 len 6848
lzo1x_decompress(buf, 1407947402...)
LZO Decompress rd=26696, wr=65536 @ 0x3705d8
nowPtr 376e22 c1 88 c2 c2 len 88c2
lzo1x_decompress(buf, 1407945492...)
LZO Decompress rd=35010, wr=65536 @ 0x376e22
nowPtr 37f6e6 c1 82 c2 e1 len 82e1
lzo1x_decompress(buf, 1407946264...)
LZO Decompress rd=33505, wr=65536 @ 0x37f6e6
nowPtr 3879c9 c1 5c c2 d5 len 5cd5
lzo1x_decompress(buf, 1407945499...)
LZO Decompress rd=23765, wr=65536 @ 0x3879c9
nowPtr 38d6a0 c1 68 c2 58 len 6858
lzo1x_decompress(buf, 1407947538...)
LZO Decompress rd=26712, wr=65536 @ 0x38d6a0
nowPtr 393efa c1 70 c2 f0 len 70f0
lzo1x_decompress(buf, 1407943756...)
LZO Decompress rd=28912, wr=65536 @ 0x393efa
nowPtr 39afec c1 5b c2 b2 len 5bb2
lzo1x_decompress(buf, 1407946782...)
LZO Decompress rd=23474, wr=65536 @ 0x39afec
nowPtr 3a0ba0 c1 66 c2 de len 66de
lzo1x_decompress(buf, 1407944338...)
LZO Decompress rd=26334, wr=65536 @ 0x3a0ba0
nowPtr 3a7280 c1 71 c2 91 len 7191
lzo1x_decompress(buf, 1407944850...)
LZO Decompress rd=29073, wr=65536 @ 0x3a7280
nowPtr 3ae413 c1 72 c2 e0 len 72e0
lzo1x_decompress(buf, 1407945477...)
LZO Decompress rd=29408, wr=65536 @ 0x3ae413
nowPtr 3b56f5 c1 65 c2 ac len 65ac
lzo1x_decompress(buf, 1407947015...)
LZO Decompress rd=26028, wr=65536 @ 0x3b56f5
nowPtr 3bbca3 c1 76 c2 7b len 767b
lzo1x_decompress(buf, 1407944597...)
LZO Decompress rd=30331, wr=65536 @ 0x3bbca3
nowPtr 3c3320 c1 7c c2 ec len 7cec
lzo1x_decompress(buf, 544279250...)
LZO Decompress rd=31980, wr=65536 @ 0x3c3320
nowPtr 3cb00e c1 77 c2 e len 770e
lzo1x_decompress(buf, 1407945504...)
LZO Decompress rd=30478, wr=65536 @ 0x3cb00e
nowPtr 3d271e c1 72 c2 21 len 7221
lzo1x_decompress(buf, 1407946128...)
LZO Decompress rd=29217, wr=65536 @ 0x3d271e
nowPtr 3d9941 c1 6d c2 ae len 6dae
lzo1x_decompress(buf, 1407945491...)
LZO Decompress rd=28078, wr=65536 @ 0x3d9941
nowPtr 3e06f1 c1 78 c2 79 len 7879
lzo1x_decompress(buf, 1407947651...)
LZO Decompress rd=30841, wr=65536 @ 0x3e06f1
nowPtr 3e7f6c c1 73 c2 d2 len 73d2
lzo1x_decompress(buf, 1407943742...)
LZO Decompress rd=29650, wr=65536 @ 0x3e7f6c
nowPtr 3ef340 c1 6c c2 32 len 6c32
lzo1x_decompress(buf, 1407947666...)
LZO Decompress rd=27698, wr=65536 @ 0x3ef340
nowPtr 3f5f74 c1 92 c2 9a len 929a
lzo1x_decompress(buf, 1407943686...)
LZO Decompress rd=37530, wr=65536 @ 0x3f5f74
nowPtr 3ff210 c1 81 c2 22 len 8122
lzo1x_decompress(buf, 1407944578...)
LZO Decompress rd=33058, wr=65536 @ 0x3ff210
nowPtr 407334 c1 5c c2 26 len 5c26
lzo1x_decompress(buf, 1407947654...)
LZO Decompress rd=23590, wr=65536 @ 0x407334
nowPtr 40cf5c c1 5e c2 e8 len 5ee8
lzo1x_decompress(buf, 1407943726...)
LZO Decompress rd=24296, wr=65536 @ 0x40cf5c
nowPtr 412e46 c1 75 c2 ab len 75ab
lzo1x_decompress(buf, 1407944728...)
LZO Decompress rd=30123, wr=65536 @ 0x412e46
nowPtr 41a3f3 c1 5a c2 74 len 5a74
lzo1x_decompress(buf, 1407947397...)
LZO Decompress rd=23156, wr=65536 @ 0x41a3f3
nowPtr 41fe69 c1 85 c2 85 len 8585
lzo1x_decompress(buf, 1407944731...)
LZO Decompress rd=34181, wr=65536 @ 0x41fe69
nowPtr 4283f0 c1 59 c2 44 len 5944
lzo1x_decompress(buf, 1407947138...)
LZO Decompress rd=22852, wr=65536 @ 0x4283f0
nowPtr 42dd36 c1 5f c2 93 len 5f93
lzo1x_decompress(buf, 1407947016...)
LZO Decompress rd=24467, wr=65536 @ 0x42dd36
nowPtr 433ccb c1 81 c2 79 len 8179
lzo1x_decompress(buf, 1407947421...)
LZO Decompress rd=33145, wr=65536 @ 0x433ccb
nowPtr 43be46 c1 4b c2 4a len 4b4a
lzo1x_decompress(buf, 1407946136...)
LZO Decompress rd=19274, wr=65536 @ 0x43be46
nowPtr 440992 c1 4c c2 3c len 4c3c
lzo1x_decompress(buf, 1407945220...)
LZO Decompress rd=19516, wr=65536 @ 0x440992
nowPtr 4455d0 c1 4b c2 54 len 4b54
lzo1x_decompress(buf, 1407944066...)
LZO Decompress rd=19284, wr=65536 @ 0x4455d0
nowPtr 44a126 c1 47 c2 6a len 476a
lzo1x_decompress(buf, 1407945880...)
LZO Decompress rd=18282, wr=65536 @ 0x44a126
nowPtr 44e892 c1 80 c2 9b len 809b
lzo1x_decompress(buf, 1407946116...)
LZO Decompress rd=32923, wr=65536 @ 0x44e892
nowPtr 45692f c1 66 c2 4e len 664e
lzo1x_decompress(buf, 1407947649...)
LZO Decompress rd=26190, wr=65536 @ 0x45692f
nowPtr 45cf7f c1 7b c2 3e len 7b3e
lzo1x_decompress(buf, 1407943729...)
LZO Decompress rd=31550, wr=65536 @ 0x45cf7f
nowPtr 464abf c1 57 c2 b2 len 57b2
lzo1x_decompress(buf, 1407944337...)
LZO Decompress rd=22450, wr=65536 @ 0x464abf
nowPtr 46a273 c1 6b c2 73 len 6b73
lzo1x_decompress(buf, 1407947269...)
LZO Decompress rd=27507, wr=65536 @ 0x46a273
nowPtr 470de8 c1 59 c2 c4 len 59c4
lzo1x_decompress(buf, 1407945754...)
LZO Decompress rd=22980, wr=65536 @ 0x470de8
nowPtr 4767ae c1 83 c2 54 len 8354
lzo1x_decompress(buf, 1407946528...)
LZO Decompress rd=33620, wr=65536 @ 0x4767ae
nowPtr 47eb04 c1 54 c2 74 len 5474
lzo1x_decompress(buf, 1407947670...)
LZO Decompress rd=21620, wr=65536 @ 0x47eb04
nowPtr 483f7a c1 3b c2 7d len 3b7d
lzo1x_decompress(buf, 1407943788...)
LZO Decompress rd=15229, wr=65536 @ 0x483f7a
nowPtr 487af9 c1 33 c2 95 len 3395
lzo1x_decompress(buf, 1407947531...)
LZO Decompress rd=13205, wr=65536 @ 0x487af9
nowPtr 48ae90 c1 41 c2 51 len 4151
lzo1x_decompress(buf, 1407947778...)
LZO Decompress rd=16721, wr=65536 @ 0x48ae90
nowPtr 48efe3 c1 5b c2 4b len 5b4b
lzo1x_decompress(buf, 1407946645...)
LZO Decompress rd=23371, wr=65536 @ 0x48efe3
nowPtr 494b30 c1 54 c2 5c len 545c
lzo1x_decompress(buf, 1407947778...)
LZO Decompress rd=21596, wr=65536 @ 0x494b30
nowPtr 499f8e c1 2d c2 40 len 2d40
lzo1x_decompress(buf, 1407943744...)
LZO Decompress rd=11584, wr=65536 @ 0x499f8e
nowPtr 49ccd0 c1 47 c2 a1 len 47a1
lzo1x_decompress(buf, 1407944834...)
LZO Decompress rd=18337, wr=65536 @ 0x49ccd0
nowPtr 4a1473 c1 4c c2 58 len 4c58
lzo1x_decompress(buf, 1407943808...)
LZO Decompress rd=19544, wr=65536 @ 0x4a1473
nowPtr 4a60cd c1 48 c2 d9 len 48d9
lzo1x_decompress(buf, 1407946271...)
LZO Decompress rd=18649, wr=65536 @ 0x4a60cd
nowPtr 4aa9a8 c1 59 c2 20 len 5920
lzo1x_decompress(buf, 1407944474...)
LZO Decompress rd=22816, wr=65536 @ 0x4aa9a8
nowPtr 4b02ca c1 5a c2 cd len 5acd
lzo1x_decompress(buf, 1407947164...)
LZO Decompress rd=23245, wr=65536 @ 0x4b02ca
nowPtr 4b5d99 c1 61 c2 bf len 61bf
lzo1x_decompress(buf, 1407947659...)
LZO Decompress rd=25023, wr=65536 @ 0x4b5d99
nowPtr 4bbf5a c1 41 c2 7c len 417c
lzo1x_decompress(buf, 1407943808...)
LZO Decompress rd=16764, wr=65536 @ 0x4bbf5a
nowPtr 4c00d8 c1 42 c2 c len 420c
lzo1x_decompress(buf, 1407944458...)
LZO Decompress rd=16908, wr=65536 @ 0x4c00d8
nowPtr 4c42e6 c1 65 c2 77 len 6577
lzo1x_decompress(buf, 1407945880...)
LZO Decompress rd=25975, wr=65536 @ 0x4c42e6
nowPtr 4ca85f c1 2c c2 3b len 2c3b
lzo1x_decompress(buf, 1407944977...)
LZO Decompress rd=11323, wr=65536 @ 0x4ca85f
nowPtr 4cd49c c1 1 c2 65 len 165
lzo1x_decompress(buf, 1407945262...)
LZO Decompress rd=357, wr=65536 @ 0x4cd49c
nowPtr 4cd603 c1 1 c2 65 len 165
lzo1x_decompress(buf, 1407945621...)
LZO Decompress rd=357, wr=65536 @ 0x4cd603
nowPtr 4cd76a c1 1 c2 65 len 165
lzo1x_decompress(buf, 1407945980...)
LZO Decompress rd=357, wr=65536 @ 0x4cd76a
nowPtr 4cd8d1 c1 12 c2 a7 len 12a7
lzo1x_decompress(buf, 1407946627...)
LZO Decompress rd=4775, wr=65536 @ 0x4cd8d1
nowPtr 4ceb7a c1 85 c2 77 len 8577
lzo1x_decompress(buf, 1407943808...)
LZO Decompress rd=34167, wr=65536 @ 0x4ceb7a
nowPtr 4d70f3 c1 86 c2 d2 len 86d2
lzo1x_decompress(buf, 1407945733...)
LZO Decompress rd=34514, wr=65536 @ 0x4d70f3
nowPtr 4df7c7 c1 6e c2 db len 6edb
lzo1x_decompress(buf, 1407945497...)
LZO Decompress rd=28379, wr=65536 @ 0x4df7c7
nowPtr 4e66a4 c1 83 c2 64 len 8364
lzo1x_decompress(buf, 1407946262...)
LZO Decompress rd=33636, wr=65536 @ 0x4e66a4
nowPtr 4eea0a c1 fe c2 97 len fe97
lzo1x_decompress(buf, 1407946012...)
LZO Decompress rd=65175, wr=65536 @ 0x4eea0a
nowPtr 4fe8a3 c1 f0 c2 e8 len f0e8
lzo1x_decompress(buf, 1407946133...)
LZO Decompress rd=61672, wr=61440 @ 0x4fe8a3
nowPtr 50d98d c1 10 c2 15 len 1015
lzo1x_decompress(buf, 1407946271...)
LZO Decompress rd=4117, wr=4096 @ 0x50d98d
nowPtr 50e9a4 c1 f0 c2 ec len f0ec
lzo1x_decompress(buf, 1407946390...)
LZO Decompress rd=61676, wr=61440 @ 0x50e9a4
nowPtr 51da92 c1 10 c2 15 len 1015
lzo1x_decompress(buf, 1407946500...)
LZO Decompress rd=4117, wr=4096 @ 0x51da92
nowPtr 51eaa9 c1 f0 c2 ec len f0ec
lzo1x_decompress(buf, 1407946651...)
LZO Decompress rd=61676, wr=61440 @ 0x51eaa9
nowPtr 52db97 c1 10 c2 16 len 1016
lzo1x_decompress(buf, 1407946761...)
LZO Decompress rd=4118, wr=4096 @ 0x52db97
nowPtr 52ebaf c1 f0 c2 f2 len f0f2
lzo1x_decompress(buf, 1407947009...)
LZO Decompress rd=61682, wr=61440 @ 0x52ebaf
nowPtr 53dca3 c1 10 c2 14 len 1014
lzo1x_decompress(buf, 1407947029...)
LZO Decompress rd=4116, wr=4096 @ 0x53dca3
nowPtr 53ecb9 c1 f0 c2 ee len f0ee
lzo1x_decompress(buf, 1407947275...)
LZO Decompress rd=61678, wr=61440 @ 0x53ecb9
nowPtr 54dda9 c1 10 c2 15 len 1015
lzo1x_decompress(buf, 1407947291...)
LZO Decompress rd=4117, wr=4096 @ 0x54dda9
nowPtr 54edc0 c1 7d c2 4d len 7d4d
lzo1x_decompress(buf, 1407946514...)
LZO Decompress rd=32077, wr=65536 @ 0x54edc0
nowPtr 556b0f c1 9 c2 3 len 903
lzo1x_decompress(buf, 1407944833...)
LZO Decompress rd=2307, wr=65536 @ 0x556b0f
nowPtr 557414 c1 10 c2 43 len 1043
lzo1x_decompress(buf, 1407944838...)
LZO Decompress rd=4163, wr=65536 @ 0x557414
nowPtr 558459 c1 14 c2 99 len 1499
lzo1x_decompress(buf, 1407945995...)
LZO Decompress rd=5273, wr=65536 @ 0x558459
nowPtr 5598f4 c1 1f c2 87 len 1f87
lzo1x_decompress(buf, 1407945862...)
LZO Decompress rd=8071, wr=19532 @ 0x5598f4
nowPtr 55b87d c1 0 c2 0 len 0
Decompressed 4777499 bytes-> 10832972 bytes
Offset Size Name
0 c0004 *.boot
c0004 100 Startup-header flags1=0x9 flags2=0 paddr_bias=0x7ffc80000000
c0104 d008 startup.*
cd10c 5c Image-header mountpoint=/
cd168 1d84 Image-directory
---- ---- Root-dirent
---- 1c usr/bin/icudt35l.dat -> /mnt/EFS_RO/icu/icudt35l.dat
---- 1c usr/HBproject/trails -> /mnt/hbuser/navigation/trace
---- 22 usr/HBproject/nobss -> /mnt/hbuser/navigation/persistence
---- 1c usr/HBproject/icudt35l.dat -> /mnt/EFS_RO/icu/icudt35l.dat
---- 16 usr/HBproject/grammar -> /mnt/hbdata/speech/tts
---- 12 usr/HBproject/flash -> /mnt/HBpersistence
---- 1e usr/Hmi/data/rw -> /mnt/HBpersistence/Hmi/data/rw
---- 17 usr/Hmi/data/ro -> /mnt/EFS_RO/Hmi/data/ro
---- f opt -> /mnt/EFS_RO/opt
---- 10 home -> /mnt/EFS_RO/home
---- ---- usr/share/wave
---- 12 mnt/persistency -> /mnt/HBpersistence
---- 16 lib/libbacktrace.so -> /lib/libbacktrace.so.1
---- 10 usr/wave -> /mnt/EFS_RO/wave
---- b HBdata -> /mnt/hbdata
---- 12 bin/ls -> /mnt/EFS_RO/bin/ls
---- b EFS_RO -> /mnt/EFS_RO
---- 14 lib/libc.so.2 -> /proc/boot/libc.so.2
---- 14 usr/lib/ldqnx.so.2 -> /proc/boot/libc.so.2
---- 12 HBpersistence -> /mnt/HBpersistence
---- a tmp -> /dev/shmem
---- 9 dev/console -> /dev/ser1
---- 9 bin/esh -> /bin/fesh
---- 8 bin/sh -> /bin/ksh
ceeec 104 etc/system/config/display_wide.conf
ceff0 a etc/L6Version.txt
cf004 65000 proc/boot/procnto-instr
134004 e2cc usr/bin/pidin
1422d0 ba4 proc/boot/.script
142e74 160 usr/share/wave/PDCBeepRearStart.wav
142fd4 1a etc/shells
143004 271b bin/sloginfo
14571f 7cb etc/videoctrl-L6.cfg
145eea 104 etc/system/config/display_special.conf
146004 67000 proc/boot/libc.so.2
---- 9 proc/boot/libc.so -> libc.so.2
1ad004 f41c proc/boot/devc-sersci
1bc420 aa6 etc/inetd.conf
1bcec6 138 etc/passwd
1bd004 1c000 lib/libecpp-ne.so.4
---- f lib/libecpp-ne.so -> libecpp-ne.so.4
1d9004 2aeac lib/dll/devg-carmine.so
203eb0 102 etc/system/config/display_narrow.conf
203fb2 52 bin/checkpersistency.sh
204004 1feb3 lib/dll/libGLES_CM.so.1
223eb7 f3 etc/system/config/img.conf
223faa 45 etc/shadow
---- f lib/dll/libGLES_CM.so -> libGLES_CM.so.1
224004 2263b lib/dll/img_codec_png.so
24663f 710 usr/share/wave/PDCBeepLoop.wav
246d4f 260 bin/createHBpersistence.sh
246faf 43 etc/ftpusers
247004 22000 lib/libsocket.so.2
---- e lib/libsocket.so -> libsocket.so.2
269004 194fd usr/lib/libgf.so.1
282501 710 usr/share/wave/PDCBeepRearLoop.wav
282c11 3c2 etc/system/config/carmine-l6-7534-1280x480.conf
---- a usr/lib/libgf.so -> libgf.so.1
283004 11c4c usr/lib/libimg.so.1
294c50 3b2 usr/share/wave/PDCBeepEnd.wav
---- b usr/lib/libimg.so -> libimg.so.1
295004 1763d lib/libasound.so.2
2ac641 3bf etc/system/config/carmine-l6-7534-800x480hb.conf
2aca00 3bd etc/system/config/carmine-l6-7534-800x480.conf
2acdbd 224 proc/boot/server.cfg
---- e lib/libasound.so -> libasound.so.2
2ad004 205bf lib/libm.so.2
2cd5c3 3ae usr/share/wave/PDCBeepRearEnd.wav
2cd971 253 etc/profile
2cdbc4 15d proc/boot/pci-l6_B001.cfg
2cdd21 156 usr/share/wave/PDCBeepStart.wav
2cde77 cb etc/layermanager.cfg
2cdf42 b4 etc/videowatchdog-L6.cfg
---- 9 lib/libm.so -> libm.so.2
2ce004 12c3e usr/lib/libffb.so.2
2e0c42 76 etc/hosts
---- b usr/lib/libffb.so -> libffb.so.2
2e1004 3000 usr/lib/libmhpfilter.so.1
---- 11 usr/lib/libmhpfilter.so -> libmhpfilter.so.1
2e4004 b666 lib/dll/deva-ctrl-hb_fpga.so
2f0004 130fe lib/libcam.so.2
303102 e14 usr/share/wave/PDCBeep.wav
---- b lib/libcam.so -> libcam.so.2
304004 57a9 usr/lib/cam-cdrom.so
30a004 33a7 usr/lib/cam-disk.so
30e004 de97 usr/lib/fs-qnx4.so
31c004 118f3 usr/lib/fs-qnx6.so
32e004 c578 usr/lib/fs-cd.so
33b004 13db8 usr/lib/fs-dos.so
34f004 11fda usr/lib/fs-udf.so
361004 269bd usr/lib/io-blk.so
388004 15000 lib/dll/dspipc-dra300.so
39d004 58f9 lib/libbacktrace.so.1
3a3004 579e bin/waitfor
3a9004 28a3 bin/mkdir
3ac004 8ae4 bin/cp
3b5004 43e8 bin/slay
3ba004 30da8 sbin/devf-generic
3eb004 483f usr/sbin/tracelogger
3f0004 579e usr/bin/on
3f6004 3db2 usr/bin/flashctl
3fa004 13e61 bin/dev-dspipc
40e004 56bd bin/fesh
414004 1d8e usr/bin/nice
416004 48e6 bin/if-test
41b004 b000 usr/bin/memifs2
426004 4000 usr/bin/slogger
42a004 14000 usr/bin/pci-sh7785
43e004 10000 usr/bin/dev-sysregs
44e004 b434 sbin/io-display
45a004 21490 sbin/io-audio
47c004 11000 usr/bin/dev-ipc
48d004 c000 usr/bin/dev-videoctrl
499004 12000 usr/bin/dev-mlb
4ab004 a000 usr/bin/dev-ssi-hbfpga
4b5004 a000 usr/bin/dev-videowatchdog
4bf004 11000 usr/bin/dev-spi-hbfpga
4d0004 1db97 usr/bin/devb-eide-hbfpga
4ee004 22000 usr/bin/vdev-eeprom
510004 8000 usr/bin/vdev-tunnelipc
518004 3a000 usr/bin/layermanager
552004 1a000 usr/bin/dev-mv2trace
56c004 2c000 usr/bin/srv-starter-QNX
598004 4a3000 usr/HBproject/CicHighAsnRoot
a3b004 2b883 bin/ksh
a67004 1cff bin/echo
a69004 14391 usr/bin/devc-ser8250hb
a7d395 3bf71 etc/splash_wide.png
ab9306 2b491 etc/splash_narrow.png
ae4797 24e66 etc/sysregs-l6-7534.cfg
b095fd 14fad etc/starter.cfg
b1e5aa 1a5d etc/termcap
b20007 f44 etc/lbt
b20f4b e08 usr/share/wave/PDCBeepRear.wav
Checksums: image=0xa2f39e37 startup=0xd0268bc500000000
Image startup_size: 53512 (0xd108)
Image stored_size: 4831360 (0x49b880)
Compressed size: 4777844 (0x48e774)
The 0x00FF7EEB is the magic number signature for the IFS file structure from the dumpifs source code, sys\startup.h. The first and second “imagefs” signatures are shown, where the first “imagefs” is the file/folder structure is linked to the IFS header.
Inspecting the 0pb shows the second “imagefs” file structure later in the file at 0x00580004, which is not dumped by dumpifs. Cutting the file with “dd skip=5767171 if=9283426A.0pb of=9283426A_2nd.bin bs=1M iflag=skip_bytes” and using dumpifs, still did not allow the imagefs to be dumped. However, as the imagefs does not appear to be compressed, simply commenting out the detection of the ifs header in dumpifs.c allows the imagefs to be dumped.
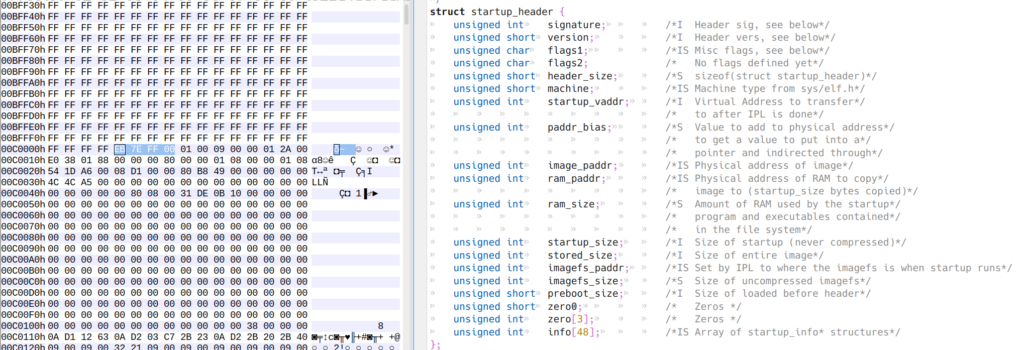
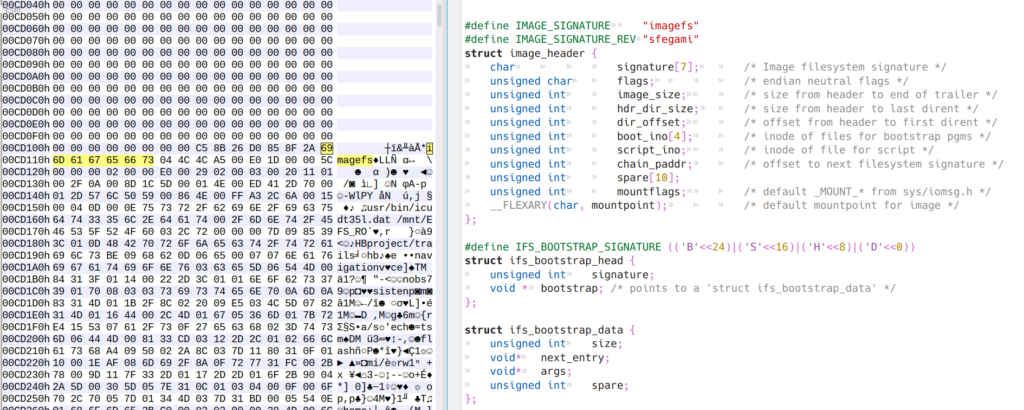
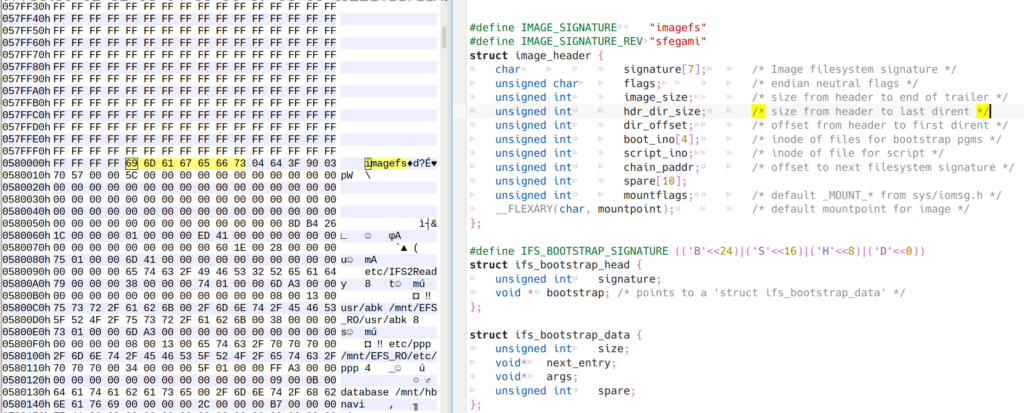

./dumpIfs.sh 9283426A_3rd.img 9283426A/
Offset Size Name
0 5c Image-header
5c 5714 Image-directory
---- ---- Root-dirent
---- ---- etc/IFS2Ready
---- 13 usr/abk -> /mnt/EFS_RO/usr/abk
---- 13 etc/ppp -> /mnt/EFS_RO/etc/ppp
---- b database -> /mnt/hbnavi
---- ---- usr/lib/terminfo/x
---- ---- usr/lib/terminfo/v
---- ---- usr/lib/terminfo/t
---- ---- usr/lib/terminfo/q
---- ---- usr/lib/terminfo/a
---- ---- usr/lib/terminfo
---- ---- usr/Hmi/otf
5770 82c usr/lib/terminfo/q/qansi-g
5f9c 44 usr/Hmi/otf/start_otf.sh
6000 b000 usr/bin/inetd
11000 d000 sbin/devc-pty
1e000 5000 sbin/mqueue
23000 1e02b sbin/io-usb
4102b eb7 etc/config/umass-enum-en5-in-car.cfg
41ee2 106 usr/bin/check_metrics.sh
42000 19000 usr/bin/vdev-medialaunch
5b000 4000 usr/bin/proc_scriptlauncher
5f000 e000 usr/bin/mme-update
6d000 8000 usr/bin/dev-nvram
75000 19dea lib/dll/img_codec_jpg.so
8edea 211 etc/fstab
8f000 4000 usr/lib/mme-imgprc-gf.so
93000 12f8e sbin/io-net
a5f8e 6d usr/bin/cleanEntertainment.sh
a6000 6000 sbin/pipe
ac000 5033 lib/dll/nfm-autoip.so
b1033 e7f etc/config/umass-enum-en5-private.cfg
b1eb2 14b usr/bin/HUShutdown.sh
b2000 a9c000 usr/HBproject/CicHighAsnSecond
b4e000 44000 usr/bin/vdev-flexgps
b92000 91000 usr/bin/ndr
c23000 8000 usr/bin/usbPowerMonitor
c2b000 35000 usr/bin/multicored
c60000 52000 usr/bin/srv_drivehandler
cb2000 b000 sbin/mcd
cbd000 42000 usr/sbin/io-media-margi
cff000 a4000 usr/sbin/srv-dvdplayer
da3000 5e000 usr/sbin/gracenote_srvr
e01000 5000 lib/dll/mdp-gracenote_client.so
e06000 b000 usr/sbin/srv-mmelauncher
e11000 8000 usr/Hmi/otf/BMWOTFagent
e19000 8000 usr/Hmi/otf/libBMWOTFapi.so.1
---- 11 usr/Hmi/otf/libBMWOTFapi.so -> libBMWOTFapi.so.1
e21000 7000 usr/Hmi/otf/libBMWOTFapi.so.2
e28000 7000 usr/Hmi/otf/libBMWOTFapi.so.3
e2f000 4000 usr/Hmi/otf/libBMWOTFdrvMCD.so.1
---- 14 usr/Hmi/otf/libBMWOTFdrvMCD.so -> libBMWOTFdrvMCD.so.1
e33000 5000 usr/Hmi/otf/libBMWOTFdrvSerial.so.1
---- 17 usr/Hmi/otf/libBMWOTFdrvSerial.so -> libBMWOTFdrvSerial.so.1
e38000 3000 usr/Hmi/otf/libBMWOTFdrvSocket.so.1
---- 17 usr/Hmi/otf/libBMWOTFdrvSocket.so -> libBMWOTFdrvSocket.so.1
e3b000 12c6000 usr/Hmi/bin/HmiMain
2101000 5e27 usr/bin/dumper
2106e27 19e etc/fstab_qnx4
2106fc5 32 etc/qkcp_export.cfg
2107000 d232 usr/bin/pidinbt
2114232 dbd etc/pre_starting_qdb.sh
2115000 be01 usr/sbin/sqlite_console
2120e01 1ea usr/bin/createQDBPaths.sh
2121000 134001 usr/sbin/mme
2255001 e1c etc/mcd.conf
2255e1d 100 etc/ecddb.ka
2255f1d 7e usr/Hmi/otf/socket.cfg
2255f9b 32 etc/qkcp_import.cfg
2255fcd 25 etc/mme.label
2256000 1f5a9 usr/sbin/qdb
22755a9 a25 etc/mmelauncher.cfg
2275fce 24 etc/ftpd.conf
2276000 fca4 usr/bin/dhcp.client
2285ca4 358 usr/mme/db/mme_connect.sql
2286000 13f22 usr/bin/fs-nfs3
2299f22 66 etc/post_starting_qdb.sh
229a000 e396 usr/bin/gunzip
22a8396 bdd etc/config/GPSairborne_L6.cfg
22a9000 358b bin/flashit
22ac58b 9d9 etc/hddmgr_qnx4.conf
22ad000 1ab0 bin/hostname
22aeab0 50d etc/ipnat.conf
22af000 1fc05 bin/qconn
22cec05 3ee etc/hfs.cfg
22cf000 2248 bin/uue
22d1248 d71 etc/ipod.cfg
22d2000 1f13 bin/cat
22d4000 2ad0 bin/mv
22d6ad0 4d9 etc/mmelauncher_upgrade_mme_10.sh
22d7000 9223 sbin/ifconfig
22e0223 b4e usr/bin/runDumper.sh
22e0d71 27f usr/bin/runPidin.sh
22e1000 8d9d lib/dll/devu-ehci.so
22e9d9d 229 etc/ipf.conf
22ea000 7369 lib/dll/devu-ohci.so
22f1369 ac7 usr/mme/db/qdb.cfg
22f2000 77fc sbin/devb-umass
22f97fc 7c3 usr/lib/terminfo/v/vt102-plus
22fa000 134c4 sbin/devc-serusb_prolific
230d4c4 abf etc/hddmgr.conf
230e000 11d56 lib/dll/devn-asix.so
2320000 e2a2 lib/dll/devn-micrel8841.so
232e2a2 950 usr/lib/terminfo/v/vs100
232ebf2 40b usr/lib/terminfo/v/vi200-f
232f000 2e000 lib/dll/npm-qnet-l4_lite.so
235d000 12000 lib/dll/devn-mlb.so
236f000 11c20 usr/bin/HBSerDev
2380c20 3cc usr/lib/terminfo/v/viewpoint
2381000 3e5d bin/mount
2385000 1a33 bin/umount
2386a33 5b4 usr/lib/terminfo/q/qnx2
2387000 50b1 bin/login
238c0b1 950 usr/lib/terminfo/x/xterm
238ca01 5d3 usr/lib/terminfo/q/qnx
238d000 288c usr/bin/rm
238f88c 746 etc/mmelauncher_upgrade_mme_29.sh
2390000 e396 bin/gzip
239e396 935 usr/lib/terminfo/q/qansi-m
239eccb 32d etc/dotMmeDotDelete.sh
239f000 1ebf4 usr/sbin/telnetd
23bdbf4 40b usr/lib/terminfo/v/visual
23be000 1714e usr/sbin/ftpd
23d514e 935 usr/lib/terminfo/q/qansi-w
23d5a83 576 etc/mmelauncher_upgrade_mme_custom_3.sh
23d6000 1f2d usr/sbin/if_up
23d8000 12d10 usr/lib/libexpat.so.2
---- d usr/lib/libexpat.so -> libexpat.so.2
23eb000 2d4e0 usr/sbin/pppd
24184e0 8fd usr/lib/terminfo/q/qansi-t
2419000 4c94 sbin/sysctl
241dc94 34d etc/mmelauncher_upgrade_mme_28.sh
241e000 72e2 sbin/route
24252e2 8f7 usr/lib/terminfo/q/qansi
2425bd9 418 usr/lib/terminfo/q/qvt101
2426000 56b71 lib/dll/npm-tcpip-v4.so
247cb71 418 usr/lib/terminfo/q/qvt108
247d000 16f82 lib/dll/npm-pppmgr.so
2494000 2000 usr/lib/libsac.so
2496000 e000 usr/lib/libpal_core.so
24a4000 8000 usr/lib/libparsercreator.so
24ac000 1d000 usr/lib/libpdiparser.so
24c9000 18000 lib/dll/lsm-ipfilter-v4.so
24e1000 9889 usr/sbin/ipf
24ea889 6de usr/lib/terminfo/q/qnxm
24eb000 82ce usr/sbin/ipnat
24f32ce 8f6 usr/lib/terminfo/x/xterm-q
24f3bc4 40a etc/mmelauncher_upgrade_mme_custom_16.sh
24f4000 733e usr/bin/vdev-fsys-dbc
24fb33e 7c0 usr/lib/terminfo/t/test
24fbafe 4d9 etc/mmelauncher_upgrade_mme_11.sh
24fc000 215b7 usr/sbin/io-fs
251d5b7 78a usr/lib/terminfo/x/xterm-m
251e000 7eba sbin/chkqnx6fs
2526000 9478 sbin/chkfsys
252f478 779 usr/lib/terminfo/v/vs100s
252fbf1 40a etc/mmelauncher_upgrade_mme_custom_17.sh
2530000 23e6 usr/bin/touch
25323e6 779 usr/lib/terminfo/x/xterms
2532b5f 49b usr/lib/terminfo/a/ansi
2533000 1795 bin/sync
2534795 6d4 usr/lib/terminfo/q/qnxw
2535000 15000 lib/libecpp-ne.so.3
---- f lib/libecpp-ne.so -> libecpp-ne.so.3
254a000 6a000 lib/libcpp.so.3
---- b lib/libcpp.so -> libcpp.so.3
25b4000 6000 usr/lib/libproject_qnxapp_collect_srvlayermanager_client.so
25ba000 bbcf lib/libusbdi.so.2
25c5bcf 409 usr/lib/terminfo/q/qvt102
---- d lib/libusbdi.so -> libusbdi.so.2
25c6000 d000 lib/dll/libfont.so.1
---- c lib/dll/libfont.so -> libfont.so.1
25d3000 25dd usr/lib/libFF-T2K-cache.so.2
25d55dd 6ab usr/lib/terminfo/q/qnxtmono
25d5c88 31e etc/mmelauncher_upgrade_mme_library_8.sh
---- 14 usr/lib/libFF-T2K-cache.so -> libFF-T2K-cache.so.2
25d6000 3707 usr/lib/libFF-T2K-fm.so.1
25d9707 6a7 usr/lib/terminfo/v/vt102
---- 11 usr/lib/libFF-T2K-fm.so -> libFF-T2K-fm.so.1
25da000 40277 usr/lib/libFF-T2K.so.2
261a277 6a7 usr/lib/terminfo/v/vt102-am
261a91e 696 usr/lib/terminfo/q/qnxt
---- e usr/lib/libFF-T2K.so -> libFF-T2K.so.2
261b000 1111b usr/lib/libz.so.2
262c11b 696 usr/lib/terminfo/q/qnxt4
262c7b1 67d usr/mme/db/mme_custom.sql
---- 9 usr/lib/libz.so -> libz.so.2
262d000 a000 lib/dll/libhiddi.so.1
---- d lib/dll/libhiddi.so -> libhiddi.so.1
2637000 5000 usr/lib/libpal_audio.so
263c000 7000 usr/lib/libpal_bt.so
2643000 2b000 usr/lib/libscp_core.so
266e000 44000 usr/lib/libsse.so
26b2000 b5000 usr/lib/libsvox.so
2767000 99000 usr/lib/libtools.so
2800000 4000 usr/lib/libaliveservice.so
2804000 4000 usr/lib/libaudiocoder.so
2808000 5000 usr/lib/libaudiocoder_ans.so
280d000 f000 usr/lib/libaudiocoder_tts.so
281c000 14000 usr/lib/libaudiomatrixservice.so
2830000 63000 usr/lib/libdsr.so
2893000 5000 usr/lib/libhostagent.so
2898000 12000 usr/lib/libmonitorservice.so
28aa000 37000 usr/lib/libprompterservice.so
28e1000 41000 usr/lib/librecognitionservice.so
2922000 a000 usr/lib/librmssservice.so
292c000 16000 usr/lib/libsaipservice.so
2942000 d000 usr/lib/libsaopservice.so
294f000 16000 usr/lib/libscfservice.so
2965000 38000 usr/lib/libspellmatcherservice.so
299d000 2000 usr/lib/libsss_config.so
299f000 25000 usr/lib/libtnservice.so
29c4000 6000 usr/lib/libunidb_sqlite3so.so
29ca000 2000 usr/lib/libhbsystime_posix_1_0.so
29cc000 11000 lib/dll/dspipc-dm642.so
29dd000 6000 lib/libdspipc.so
29e3000 c000 usr/lib/libmldr.so
29ef000 10bc8 usr/bin/srv-hddmgr
29ffbc8 406 etc/mmelauncher_upgrade_mme_custom_10.sh
2a00000 5546 bin/inflator
2a05546 63e etc/mmelauncher_upgrade_mme_custom_27.sh
2a05b84 406 etc/mmelauncher_upgrade_mme_custom_11.sh
2a06000 9d31 usr/lib/fs-nt.so
2a10000 73000 usr/lib/libsqlite3.so.1
---- f usr/lib/libsqlite3.so -> libsqlite3.so.1
2a83000 6000 usr/lib/libthirdparty_qdb_icu_3_5_bmw.so
---- 20 usr/lib/libthirdparty_qdb_icu_3_5.so -> libthirdparty_qdb_icu_3_5_bmw.so
2a89000 123000 usr/lib/libthirdparty_icu_3_5_bmw.so
---- 1c usr/lib/libthirdparty_icu_3_5.so -> libthirdparty_icu_3_5_bmw.so
2bac000 d000 usr/lib/libasiacollation.so
2bb9000 47fc usr/bin/qdblauncher
2bbd7fc 5d3 usr/lib/terminfo/q/qnx4
2bbe000 4000 usr/lib/libmmfilter.so.1
---- 10 usr/lib/libmmfilter.so -> libmmfilter.so.1
2bc2000 b000 usr/lib/libmmedia.so.1
---- e usr/lib/libmmedia.so -> libmmedia.so.1
2bcd000 4000 usr/lib/libaoi.so.1
---- b usr/lib/libaoi.so -> libaoi.so.1
2bd1000 b000 usr/lib/libmme.so.1
---- b usr/lib/libmme.so -> libmme.so.1
2bdc000 8000 usr/lib/libqdb.so.1
---- b usr/lib/libqdb.so -> libqdb.so.1
2be4000 93000 usr/lib/libxml2.so.1
---- c usr/lib/libxml2.so -> libxml2.so.1
2c77000 e000 lib/dll/mmedia/aac_parser.so
2c85000 5000 lib/dll/mmedia/cdda_parser.so
2c8a000 5000 lib/dll/mmedia/cdda_streamer.so
2c8f000 4000 lib/dll/mmedia/fildes_streamer.so
2c93000 5000 lib/dll/mmedia/media_streamer.so
2c98000 f000 lib/dll/mmedia/mmipc_writer.so
2ca7000 f000 lib/dll/mmedia/mpega_parser.so
2cb6000 17000 lib/dll/mmedia/mp4_parser.so
2ccd000 4000 lib/dll/mmedia/queue_filter.so
2cd1000 5000 lib/dll/mmedia/stream_reader.so
2cd6000 43000 lib/dll/mmedia/wma9_parser.so
2d19000 2f2a5 usr/sbin/mmecli
2d482a5 5b4 usr/lib/terminfo/q/qnxs2
2d48859 56c usr/lib/terminfo/v/vt100
2d49000 850e usr/sbin/qdbc
2d5150e 56c usr/lib/terminfo/v/vt100-am
2d51a7a 569 etc/mmelauncher_upgrade_mme_custom_2.sh
2d52000 5976 usr/sbin/fileset
2d57976 55b usr/lib/terminfo/q/qnxt2
2d58000 9000 lib/dll/mmedia/dvd_eventer.so
2d61000 14000 lib/dll/mmedia/mmipc_encoder.so
2d75000 e000 lib/dll/mmedia/muxer.so
2d83000 7000 lib/dll/mmedia/parser_dvd.so
2d8a000 b000 lib/dll/mmedia/parser_mpgvfile.so
2d95000 8000 lib/dll/mmedia/parser_vcd.so
2d9d000 5000 lib/dll/mmedia/rawfile_writer.so
2da2000 8000 lib/dll/mmedia/reader_dvd.so
2daa000 a000 lib/dll/mmedia/streamer_dvd.so
2db4000 4000 lib/dll/mmedia/tmpfile_streamer.so
2db8000 5000 lib/dll/mmedia/wms_control.so
2dbd000 3000 lib/dll/mmedia/wms_streamer.so
2dc0000 aa3d lib/dll/mmedia/writer_dm642.so
2dcaa3d 4d9 etc/mmelauncher_upgrade_mme_12.sh
2dcb000 9000 lib/dll/mmedia/dvd_eventer.so
2dd4000 1363f lib/dll/mmedia/dmb_parser.so
2de763f 4d9 etc/mmelauncher_upgrade_mme_13.sh
2de7b18 4d9 etc/mmelauncher_upgrade_mme_14.sh
2de8000 3000 lib/dll/mmedia/dmb_streamer.so
2deb000 11000 lib/dll/libAppFramework.A.so
2dfc000 1e000 lib/dll/libCoreFramework.A.so
2e1a000 13000 lib/dll/libhmibidi.so
2e2d000 72000 lib/dll/libcpp.so.4
---- b lib/dll/libcpp.so -> libcpp.so.4
2e9f000 6e34 usr/bin/apnl6
2ea6000 920a64 usr/bin/apnnav
37c6a64 4d9 etc/mmelauncher_upgrade_mme_15.sh
37c7000 7cec usr/bin/VssServer
37cf000 5a000 usr/lib/libcpp-ne.so.4
---- e usr/lib/libcpp-ne.so -> libcpp-ne.so.4
3829000 2000 lib/dll/libbmwqkcp.so.1
---- f lib/dll/libbmwqkcp.so -> libbmwqkcp.so.1
382b000 a000 usr/bin/scp
3835000 8e0e etc/mmelauncher_upgrade_mme_22.sh
383de0e 88e8 etc/mme.conf
38466f6 8683 etc/mmelauncher_upgrade_mme_library_6.sh
384ed79 8460 etc/sss/ar_XA/default.cfg
38571d9 8460 etc/sss/de_DE/default.cfg
385f639 8460 etc/sss/el_GR/default.cfg
3867a99 8460 etc/sss/en_GB/default.cfg
386fef9 8460 etc/sss/en_US/default.cfg
3878359 8460 etc/sss/fr_FR/default.cfg
38807b9 8460 etc/sss/es_ES/default.cfg
3888c19 8460 etc/sss/hu_HU/default.cfg
3891079 8460 etc/sss/it_IT/default.cfg
38994d9 8460 etc/sss/nl_NL/default.cfg
38a1939 8460 etc/sss/pl_PL/default.cfg
38a9d99 8460 etc/sss/pt_PT/default.cfg
38b21f9 8460 etc/sss/ru_RU/default.cfg
38ba659 8460 etc/sss/sv_SE/default.cfg
38c2ab9 8460 etc/sss/tr_TR/default.cfg
38caf19 8460 etc/sss/ja_JP/default.cfg
38d3379 8460 etc/sss/ko_KR/default.cfg
38db7d9 8053 etc/sss/en_RR/default.cfg
38e382c 7d86 usr/mme/db/mme.sql
38eb5b2 2f34 usr/mme/db/mme_library.sql
38ee4e6 2372 etc/io-media-margi.cfg
38f0858 1ef8 usr/mme/db/mme_data.sql
38f2750 1a80 etc/mmelauncher_upgrade_mme_custom_26.sh
38f41d0 198c usr/mme/db/mme_mp3_speech.sql
38f5b5c 10f1 usr/mme/db/mme_temp.sql
38f6c4d 4d9 etc/mmelauncher_upgrade_mme_16.sh
38f7126 4d9 etc/mmelauncher_upgrade_mme_17.sh
38f75ff 4d9 etc/mmelauncher_upgrade_mme_18.sh
38f7ad8 4d9 etc/mmelauncher_upgrade_mme_19.sh
38f7fb1 4d9 etc/mmelauncher_upgrade_mme_20.sh
38f848a 4d9 etc/mmelauncher_upgrade_mme_21.sh
38f8963 4d9 etc/mmelauncher_upgrade_mme_23.sh
38f8e3c 4d9 etc/mmelauncher_upgrade_mme_24.sh
38f9315 4d9 etc/mmelauncher_upgrade_mme_25.sh
38f97ee 4d9 etc/mmelauncher_upgrade_mme_26.sh
38f9cc7 4d9 etc/mmelauncher_upgrade_mme_27.sh
38fa1a0 4d6 etc/mmelauncher_upgrade_mme_0.sh
38fa676 4d6 etc/mmelauncher_upgrade_mme_1.sh
38fab4c 4d6 etc/mmelauncher_upgrade_mme_2.sh
38fb022 4d6 etc/mmelauncher_upgrade_mme_3.sh
38fb4f8 4d6 etc/mmelauncher_upgrade_mme_4.sh
38fb9ce 4d6 etc/mmelauncher_upgrade_mme_5.sh
38fbea4 4d6 etc/mmelauncher_upgrade_mme_6.sh
38fc37a 4d6 etc/mmelauncher_upgrade_mme_7.sh
38fc850 4d6 etc/mmelauncher_upgrade_mme_8.sh
38fcd26 4d6 etc/mmelauncher_upgrade_mme_9.sh
38fd1fc 406 etc/mmelauncher_upgrade_mme_custom_12.sh
38fd602 406 etc/mmelauncher_upgrade_mme_custom_13.sh
38fda08 406 etc/mmelauncher_upgrade_mme_custom_14.sh
38fde0e 406 etc/mmelauncher_upgrade_mme_custom_15.sh
38fe214 406 etc/mmelauncher_upgrade_mme_custom_19.sh
38fe61a 406 etc/mmelauncher_upgrade_mme_custom_20.sh
38fea20 406 etc/mmelauncher_upgrade_mme_custom_21.sh
38fee26 406 etc/mmelauncher_upgrade_mme_custom_22.sh
38ff22c 406 etc/mmelauncher_upgrade_mme_custom_23.sh
38ff632 406 etc/mmelauncher_upgrade_mme_custom_24.sh
38ffa38 406 etc/mmelauncher_upgrade_mme_custom_25.sh
38ffe3e 403 etc/mmelauncher_upgrade_mme_custom_18.sh
3900241 401 etc/mmelauncher_upgrade_mme_custom_4.sh
3900642 401 etc/mmelauncher_upgrade_mme_custom_5.sh
3900a43 401 etc/mmelauncher_upgrade_mme_custom_6.sh
3900e44 401 etc/mmelauncher_upgrade_mme_custom_7.sh
3901245 401 etc/mmelauncher_upgrade_mme_custom_8.sh
3901646 401 etc/mmelauncher_upgrade_mme_custom_9.sh
3901a47 3bc etc/mmelauncher_upgrade_mme_library_0.sh
3901e03 3bc etc/mmelauncher_upgrade_mme_library_1.sh
39021bf 3bc etc/mmelauncher_upgrade_mme_library_2.sh
390257b 3bc etc/mmelauncher_upgrade_mme_library_3.sh
3902937 3bc etc/mmelauncher_upgrade_mme_library_4.sh
3902cf3 3bc etc/mmelauncher_upgrade_mme_library_5.sh
39030af 3bc etc/mmelauncher_upgrade_mme_library_7.sh
390346b 3b6 etc/mmelauncher_upgrade_mme_custom_0.sh
3903821 3b6 etc/mmelauncher_upgrade_mme_custom_1.sh
3903bd7 389 usr/lib/terminfo/v/vt52
Checksums: image=0x3f90308f
ipos=0 spos=0xffffffff ihdr.image_size=59785060 - sizeof(stlr) = 59785056
Image startup_size: 0 (0x0)
Image stored_size: 0 (0x0)
Compressed size: -4 (0xfffffffc)
Success, the full structure is dumped, and the “CicHighAsnSecond” appears to hold the navigation elf.
CicHighAsnSecond Disassembly
3. Disassemble “CicHighAsnSecond” with Ghidra. For some reason, this seems to take a really long time to fully process.
4. Look for common byte strings used in encryption routines. The first one I came across was the MD5 init seed “0x67452301”, and used it to locate the main Key Routine.
5. The unique vehicle RSA Key is located in /mnt/persistence and a copy of the Navigation key is saved on the hard drive (partition 10 – hbdebug) in the data03 file. Following the address reference (labeled FSC_TYPE_1B_CIC) goes to data “0x01 0x00 0x1B 0x00”.

6. I added function names for the core key routines to better understand the process. When following memory address links, I made an assumption that two of the locations were RSA E and Modulo, based on the size of the data and how it is referenced.

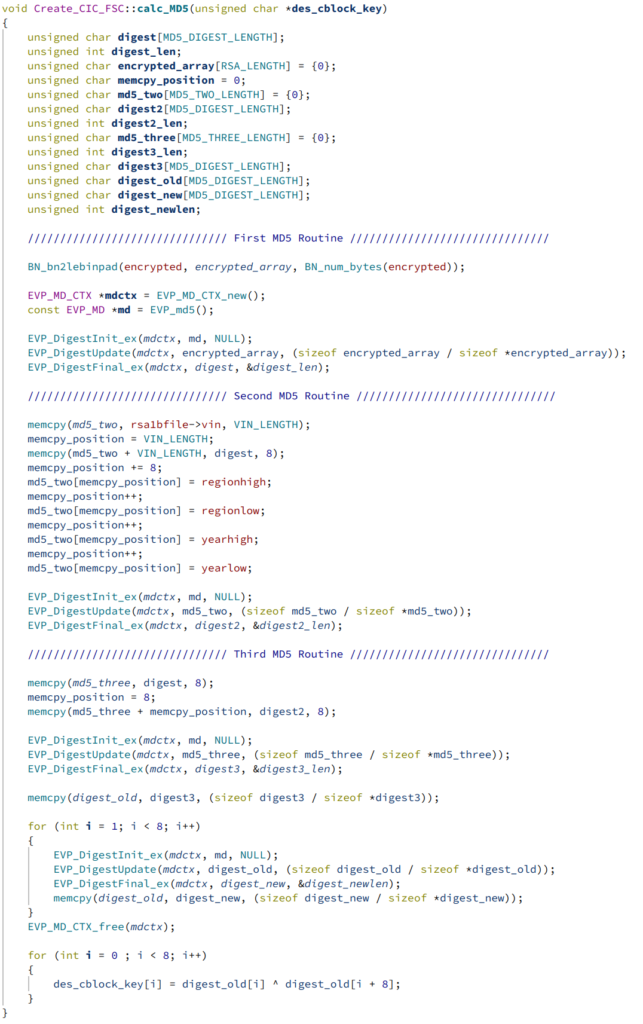
6. Once the functions were labelled, it was not difficult to determine that the overall process to generate a navigation key is:
A. Get the vehicle specifc RSA key from the 1B file.
B. Get the vehicle VIN.
C. RSA Mod Exp : The vehicle specific RSA Key with the hardcoded RSA E and Modulo.
D. First MD5 Hash : MD5 hash of the result from RSA Mod Exp.
E. Second MD5 Hash : MD5 hash of the VIN and the Map Region and Year (Looked online and found that the Region and Year are hex codes from the Lookup.xml file)
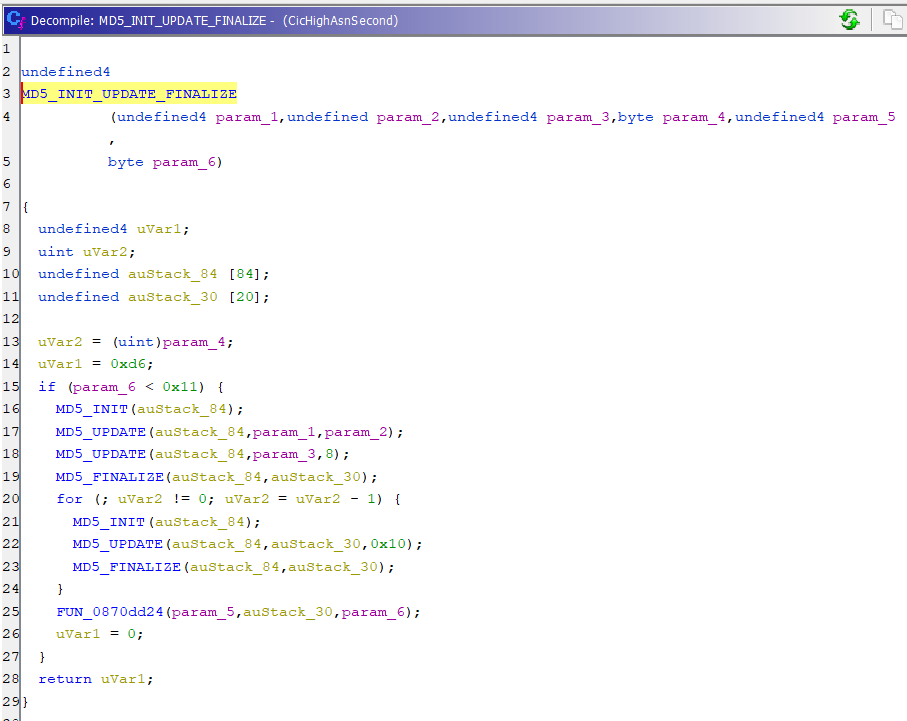
F. Third MD5 Hash : A looped combination of the First and Second MD5 Hash.
G. DES : Use the result from the Third MD5 Hash to create a DES Key that encrypts a message containing the Map Region and Year.
H. ASCII Conversion : Convert the binary result from the DES encryption into an 20-character ASCII key.
7. The overall key generation was implemented as pictured
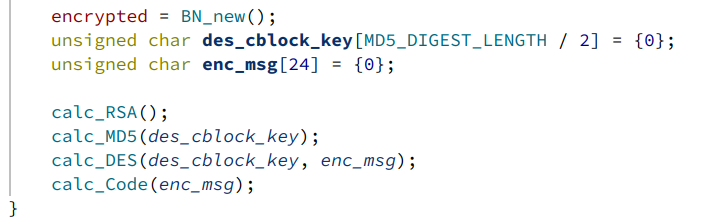
8. Following the third MD5 subroutine shows the MD5 digest being hashed multiple times, and was reimplemented as pictured.